The SpiKey attack: How to copy keys using sound
Por um escritor misterioso
Last updated 17 julho 2024

The SpiKey attack: How one can copy a key using a phone recording of the sound of the clicks the key makes during insertion into a lock.
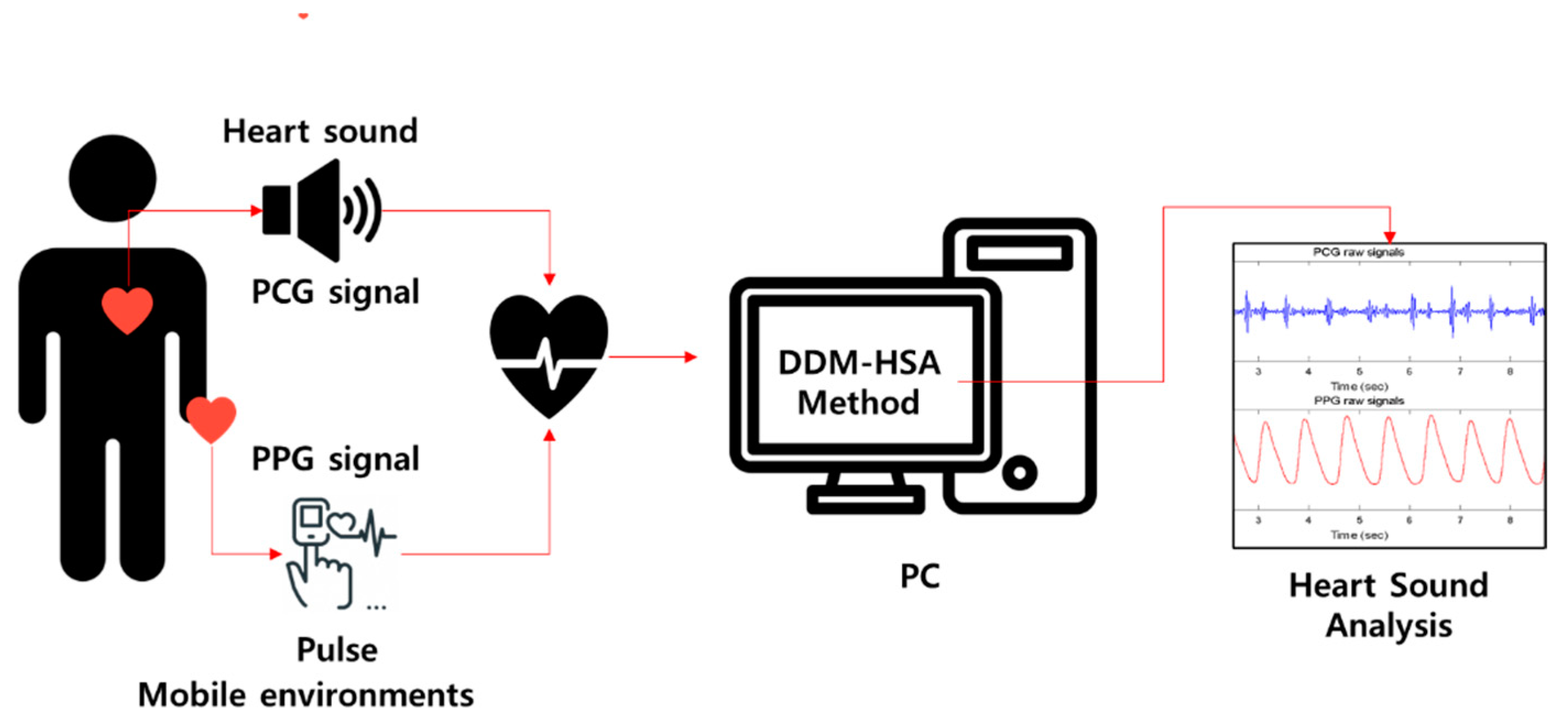
Sensors, Free Full-Text
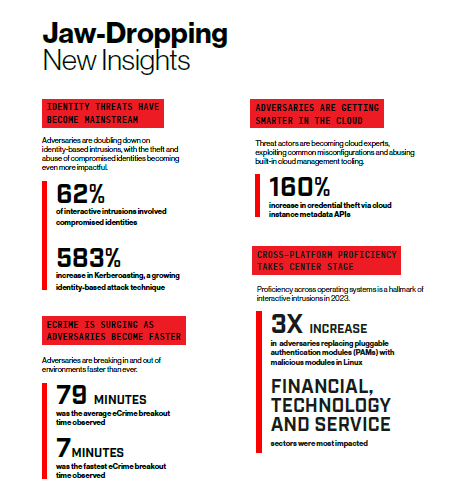
Identity-Based Attacks and Hands-on-Keyboard Activity on the Rise

What is Malware? Malware Definition, Types and Protection

What is a Content Experience Platform?

A mathematical model for the interaction of anisotropic turbulence with a rigid leading edge, Journal of Fluid Mechanics

The Top 20 Security Predictions for 2020

The 40 greatest synth sounds of all time - ranked!

Cell Membrane-Coated Mimics: A Methodological Approach for Fabrication, Characterization for Therapeutic Applications, and Challenges for Clinical Translation

Almost 300% rise in cyber attacks in India in 2020, govt tells Parliament

Top 10 Noise Gate VST Plugins 2023 (+ 6 FREE Free Tools)

Segmentation, trace denoising and spike extraction framework. (A) Mask

7 Best File Integrity Monitoring (FIM) Tools for 2023 (Paid & Free)
Recomendado para você
-
 Buy MX Keys S Keyboard - Full-Size17 julho 2024
Buy MX Keys S Keyboard - Full-Size17 julho 2024 -
 CompX Chicago 1250 - 1499 Keys17 julho 2024
CompX Chicago 1250 - 1499 Keys17 julho 2024 -
 Tiffany Keys modern keys open round key pendant in 18k gold with diamonds, mini.17 julho 2024
Tiffany Keys modern keys open round key pendant in 18k gold with diamonds, mini.17 julho 2024 -
 Dog Door Keys, Accessories17 julho 2024
Dog Door Keys, Accessories17 julho 2024 -
 Key - Lockwiki17 julho 2024
Key - Lockwiki17 julho 2024 -
 House and Antique Keys • Wessex Locksmiths17 julho 2024
House and Antique Keys • Wessex Locksmiths17 julho 2024 -
 5 Keys to Submission Success - Vintage17 julho 2024
5 Keys to Submission Success - Vintage17 julho 2024 -
 KeySmart - The Best Compact Key Holder17 julho 2024
KeySmart - The Best Compact Key Holder17 julho 2024 -
 Car key - Wikipedia17 julho 2024
Car key - Wikipedia17 julho 2024 -
The Key to the City of Springfield17 julho 2024
você pode gostar
-
 Honey We Have Guests Bring Out The Fine China GIF - Honey We Have Guests Bring Out The Fine China Man Face - Discover & Share GIFs17 julho 2024
Honey We Have Guests Bring Out The Fine China GIF - Honey We Have Guests Bring Out The Fine China Man Face - Discover & Share GIFs17 julho 2024 -
 SIP - Sala de Informática Pedagógica: JOGOS EDUCATIVOS - ESCOLA GAMES17 julho 2024
SIP - Sala de Informática Pedagógica: JOGOS EDUCATIVOS - ESCOLA GAMES17 julho 2024 -
 Blade - A free to use dashboard for open access to data about17 julho 2024
Blade - A free to use dashboard for open access to data about17 julho 2024 -
 Summer Programs Iowa State University Extension and Outreach17 julho 2024
Summer Programs Iowa State University Extension and Outreach17 julho 2024 -
Rowebb Ltd17 julho 2024
-
![mochi buzzcut [grand piece online] on Make a GIF](https://i.makeagif.com/media/11-03-2021/cYi_2A.gif) mochi buzzcut [grand piece online] on Make a GIF17 julho 2024
mochi buzzcut [grand piece online] on Make a GIF17 julho 2024 -
 Estrelas Radiantes - Pokemon - Epic Game - A loja de card game mais ÉPICA do Brasil!17 julho 2024
Estrelas Radiantes - Pokemon - Epic Game - A loja de card game mais ÉPICA do Brasil!17 julho 2024 -
 Boneca Barbie Colecionável Fashionista Vestido Rosa Xadrez - MKP - Toyshow Tudo de Marvel DC Netflix Geek Funko Pop Colecionáveis17 julho 2024
Boneca Barbie Colecionável Fashionista Vestido Rosa Xadrez - MKP - Toyshow Tudo de Marvel DC Netflix Geek Funko Pop Colecionáveis17 julho 2024 -
 Blazing Angels: Squadrons of WWII - Playstation 3 – Retro Raven Games17 julho 2024
Blazing Angels: Squadrons of WWII - Playstation 3 – Retro Raven Games17 julho 2024 -
Editora Intrínseca - Na série de jogos Five nights at Freddy's, o jogador assume o papel de um segurança contratado para tomar conta de uma pizzaria durante a noite, enquanto os animatrônicos17 julho 2024

