Malware analysis Malicious activity
Por um escritor misterioso
Last updated 20 junho 2024

Malware Analysis: Steps & Examples - CrowdStrike

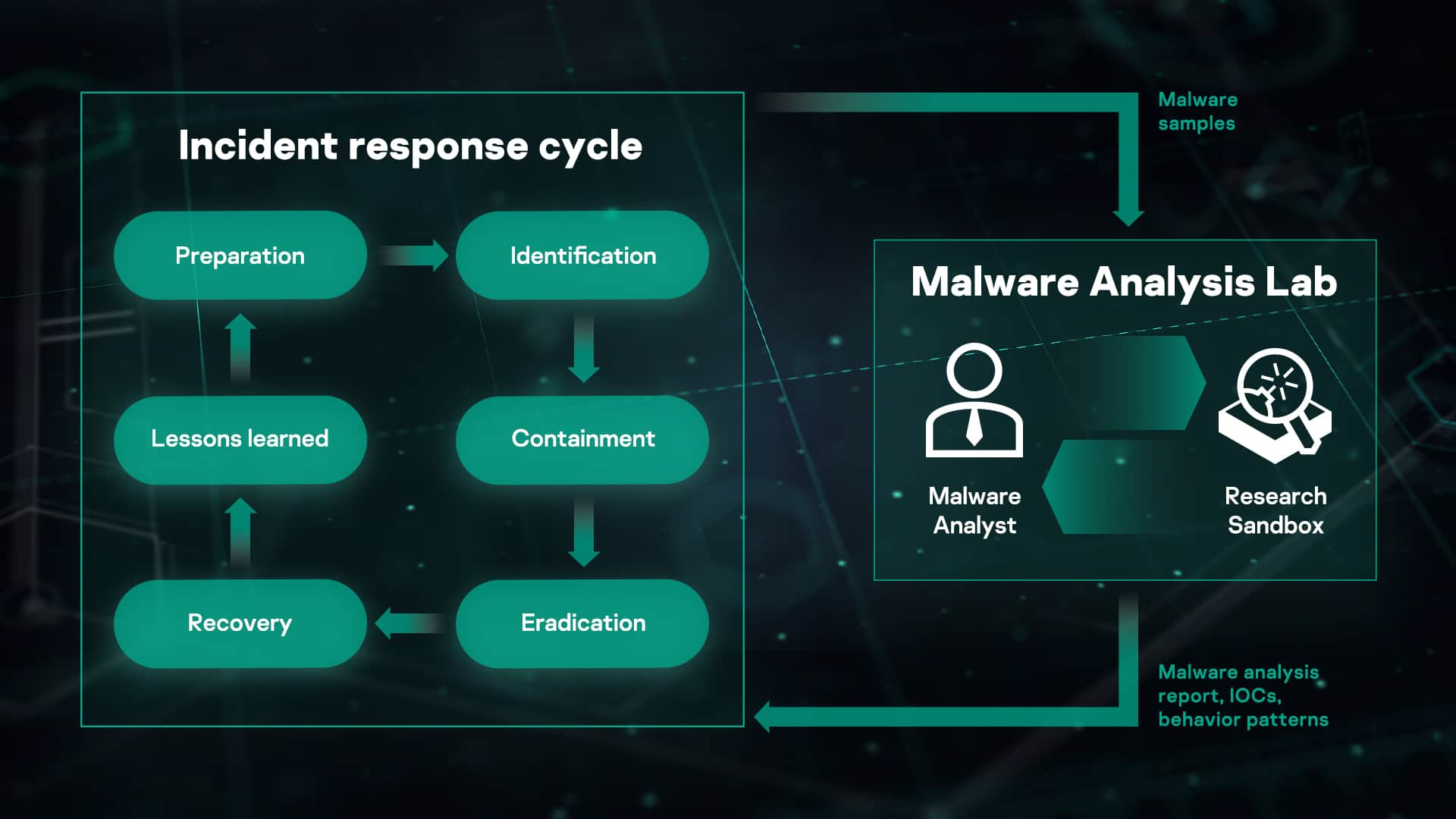
Malware Analysis Benefits Incident Response

ReversingLabs Malware Lab: Detect, classify, analyze, and respond
Malware analysis
Interactive Online Malware Sandbox
Advanced Automated Malware Analysis – Kaspersky Research Sandbox

Robust Malware Detection Models: Learning From Adversarial Attacks

Complex 'NKAbuse' Malware Uses Blockchain to Hide on Linux, IoT
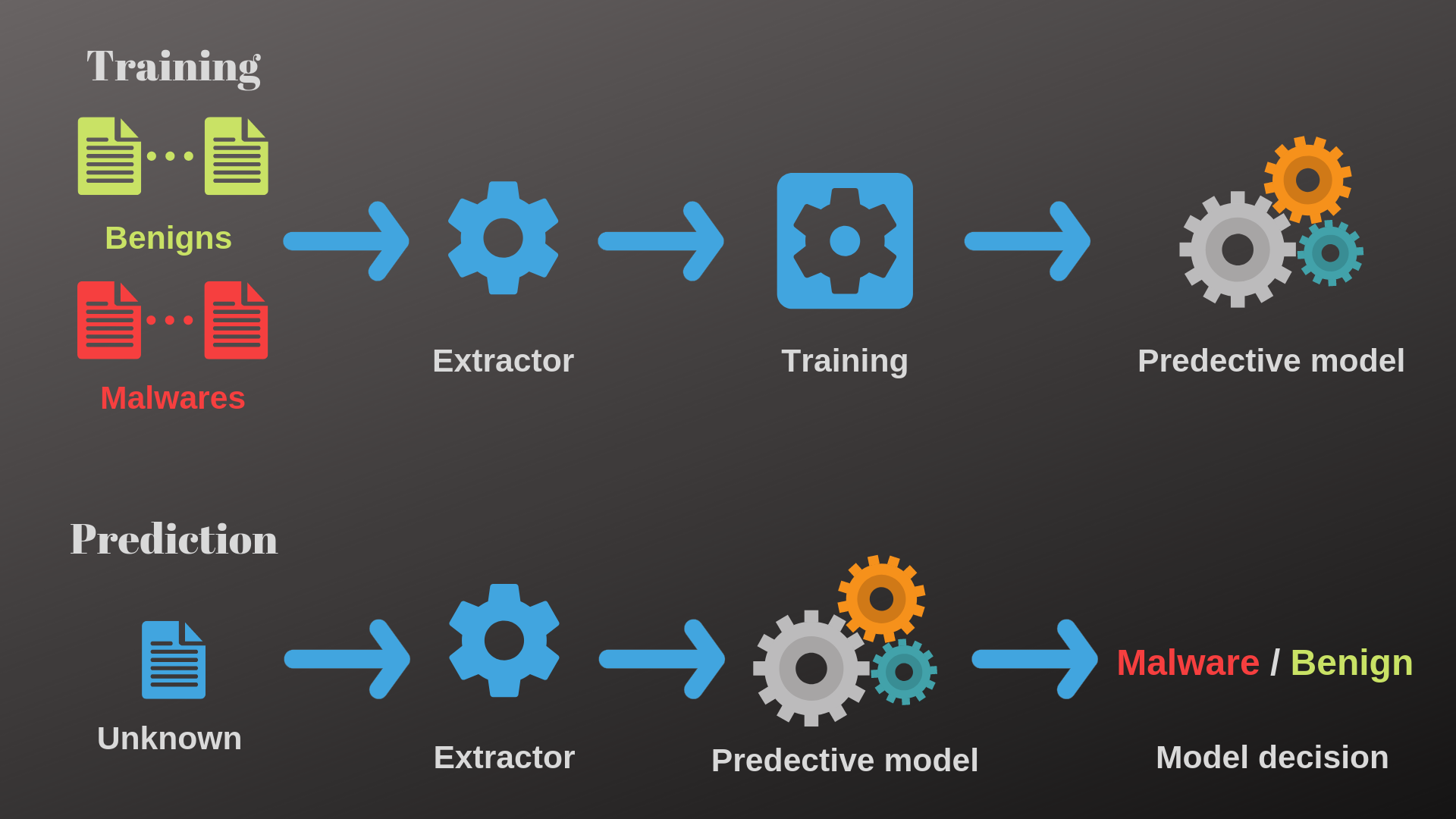
Feature Extraction and Detection of Malwares Using Machine

AlienVault - Open Threat Exchange
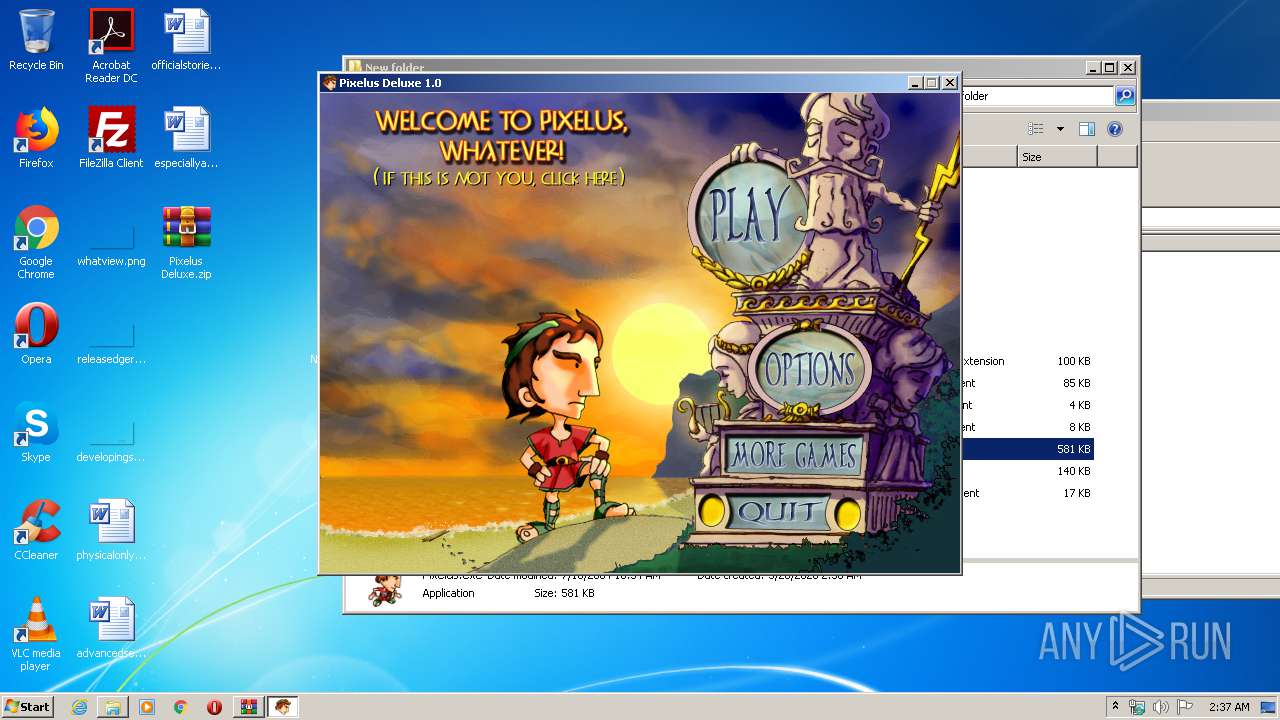
Malware analysis Pixelus Deluxe.zip Malicious activity
MetaDefender Cloud Advanced threat prevention and detection

PROUD-MAL: static analysis-based progressive framework for deep
Learning Malware Analysis: Explore the concepts, tools, and techniques to analyze and investigate Windows malware: 9781788392501: A,

Learning Malware Analysis: Explore the concepts, tools, and techniques to analyze and investigate Windows malware

Info stealers and how to protect against them
Recomendado para você
-
![200TH VIDEO] BonziBUDDY Episode #1 - Linux Edition](https://i.ytimg.com/vi/Y9OiTK_mVZk/hqdefault.jpg?v=6394aada) 200TH VIDEO] BonziBUDDY Episode #1 - Linux Edition20 junho 2024
200TH VIDEO] BonziBUDDY Episode #1 - Linux Edition20 junho 2024 -
 Yeah open source and stuff, but can Linux make this glorious sight20 junho 2024
Yeah open source and stuff, but can Linux make this glorious sight20 junho 2024 -
 Bonzi Windows, Mac, Linux game - Indie DB20 junho 2024
Bonzi Windows, Mac, Linux game - Indie DB20 junho 2024 -
 Bonzi Buddy has infected Windows 10 computer! : r/windowsmemes20 junho 2024
Bonzi Buddy has infected Windows 10 computer! : r/windowsmemes20 junho 2024 -
Purple linux icon - Free purple operating system icons20 junho 2024
-
 BonziBUDDY Episode #6 - Linux Edition20 junho 2024
BonziBUDDY Episode #6 - Linux Edition20 junho 2024 -
 Put A Yubikey On It! :: Patrick Cable20 junho 2024
Put A Yubikey On It! :: Patrick Cable20 junho 2024 -
 BonziBuddy reviews - Jokes & Funny Stuff - Neowin20 junho 2024
BonziBuddy reviews - Jokes & Funny Stuff - Neowin20 junho 2024 -
 Is Bonzi Buddy a virus? - Quora20 junho 2024
Is Bonzi Buddy a virus? - Quora20 junho 2024 -
 Johan F. Hoorn Henriette C. van Vugt AAMAS 2004 New York The20 junho 2024
Johan F. Hoorn Henriette C. van Vugt AAMAS 2004 New York The20 junho 2024
você pode gostar
-
 A ORIGEM DE MIRACULOUS LADYBUG 🐞 Anime e HQs ✨️20 junho 2024
A ORIGEM DE MIRACULOUS LADYBUG 🐞 Anime e HQs ✨️20 junho 2024 -
 Filme As Marvels fracassa nas bilheterias globais - O Herói20 junho 2024
Filme As Marvels fracassa nas bilheterias globais - O Herói20 junho 2024 -
 HAIKYU!! TO THE TOP TRAILER OFICIAL20 junho 2024
HAIKYU!! TO THE TOP TRAILER OFICIAL20 junho 2024 -
/read-avatar-the-last-airbender-comics-online-free-0565.jpg) Read Comics Online Free - Avatar The Last Airbender Comic Book Issue #015 - Page 3920 junho 2024
Read Comics Online Free - Avatar The Last Airbender Comic Book Issue #015 - Page 3920 junho 2024 -
 EDENS ZERO, Official Trailer20 junho 2024
EDENS ZERO, Official Trailer20 junho 2024 -
 Francana x Grêmio: saiba onde assistir jogo da Copinha20 junho 2024
Francana x Grêmio: saiba onde assistir jogo da Copinha20 junho 2024 -
 The Last Of Us Remastered para PS4 - Mídia Digital - Minutegames20 junho 2024
The Last Of Us Remastered para PS4 - Mídia Digital - Minutegames20 junho 2024 -
YALL THIS IS A TUT ON HOW TO PLAY ROBLOX ON SCHOOL COMPUTER20 junho 2024
-
Exploração espacial digital: a era do Space Sim20 junho 2024
-
 New Shift Code Gets Borderlands 2, 3, and Tiny Tina's Wonderlands20 junho 2024
New Shift Code Gets Borderlands 2, 3, and Tiny Tina's Wonderlands20 junho 2024

