Malware analysis Malicious activity
Por um escritor misterioso
Last updated 16 julho 2024


AlienVault - Open Threat Exchange
Krebs on Security – In-depth security news and investigation

What is Malware? Definition, Types, Prevention - TechTarget

Malware Analysis - What is, Benefits & Types (Easily Explained)
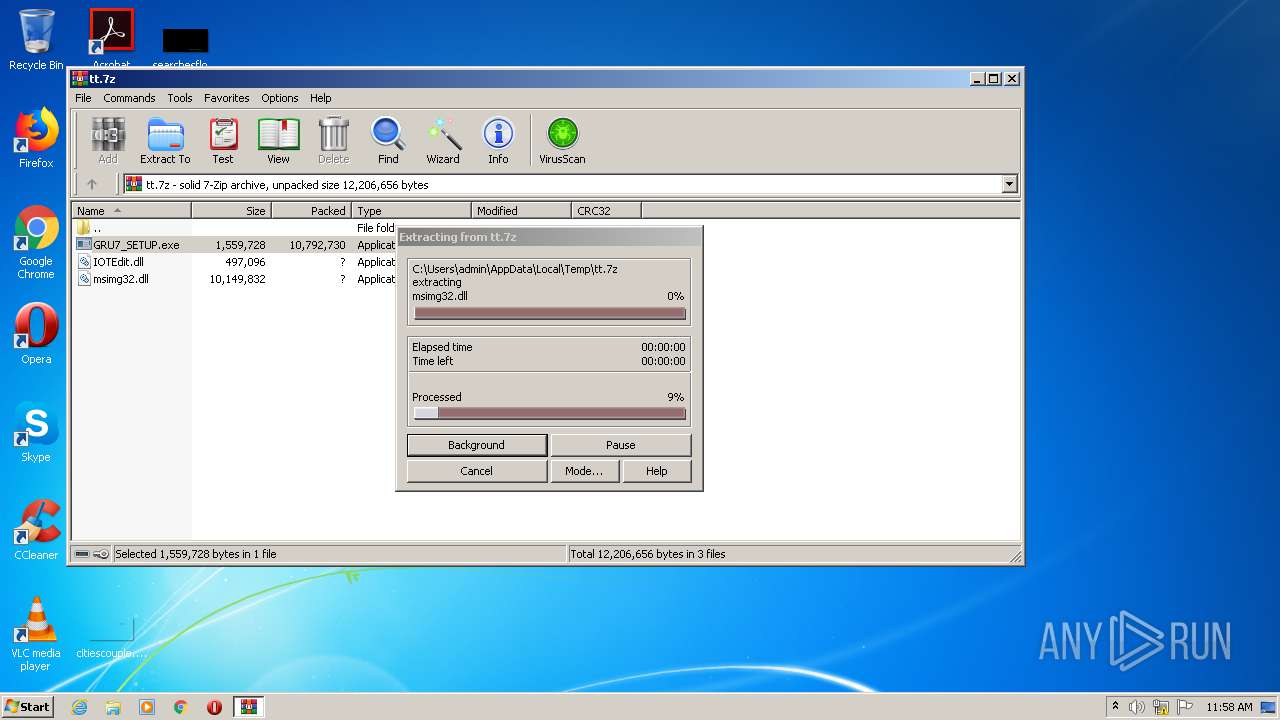
Malware analysis tt.7z Malicious activity

How to build a malware analysis sandbox with Elastic Security

PROUD-MAL: static analysis-based progressive framework for deep

Malware Analysis: Steps & Examples - CrowdStrike

Playbook of the Week: Malware Investigation and Response - Palo

Security Orchestration Use Case: Automating Malware Analysis

Routers Roasting on an Open Firewall: the KV-botnet Investigation

Remediation and Malware Detection Overview

Malware Analysis: Steps & Examples - CrowdStrike
Recomendado para você
-
 Synapse X16 julho 2024
Synapse X16 julho 2024 -
 ROBLOX SYNAPSE X CRACKED, UNDETECTED - NO BAN + TUTORIAL16 julho 2024
ROBLOX SYNAPSE X CRACKED, UNDETECTED - NO BAN + TUTORIAL16 julho 2024 -
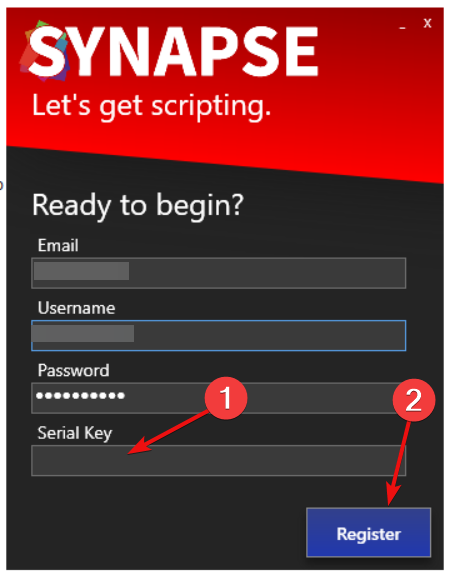 Synapse X Discord is not Working: 4 Game Changing Solutions16 julho 2024
Synapse X Discord is not Working: 4 Game Changing Solutions16 julho 2024 -
 Synapse X CRACKED! 2020 NEW NO VIRUS WORKING FREE DOWNLOAD + KEY! : r/robloxhackers16 julho 2024
Synapse X CRACKED! 2020 NEW NO VIRUS WORKING FREE DOWNLOAD + KEY! : r/robloxhackers16 julho 2024 -
GitHub - S4W77/Synapse-X-Keys: Free Synapse Serial Keys16 julho 2024
-
 Can I change Synapse shortcut to Super/Windows key alone? - Ask Ubuntu16 julho 2024
Can I change Synapse shortcut to Super/Windows key alone? - Ask Ubuntu16 julho 2024 -
![Another Synapse X Key [Giveaway][ReadDescription]](https://i.ytimg.com/vi/oCncFCniH3s/maxresdefault.jpg) Another Synapse X Key [Giveaway][ReadDescription]16 julho 2024
Another Synapse X Key [Giveaway][ReadDescription]16 julho 2024 -
 Synapse X16 julho 2024
Synapse X16 julho 2024 -
 Can Someone give me a synapse x key? - WRD Community16 julho 2024
Can Someone give me a synapse x key? - WRD Community16 julho 2024 -
Alternative pipeline parametrization for Azure Synapse Analytics – Paul Hernandez playing with Data16 julho 2024
você pode gostar
-
 Download Appreciating the Vast Possibilities that Roblox Offers Wallpaper16 julho 2024
Download Appreciating the Vast Possibilities that Roblox Offers Wallpaper16 julho 2024 -
 Worms: The Director's Cut - Wikipedia16 julho 2024
Worms: The Director's Cut - Wikipedia16 julho 2024 -
 O Caminho dos Reis, de Brandon Sanderson, chega ao Brasil em Setembro - Team Comics16 julho 2024
O Caminho dos Reis, de Brandon Sanderson, chega ao Brasil em Setembro - Team Comics16 julho 2024 -
Federação Angolana de Xadrez - CALENDÁRIO DE ACTIVIDADES DA FAX16 julho 2024
-
 Anime drawings on X: super saiyan 3 Goku drawing #anime #dbz16 julho 2024
Anime drawings on X: super saiyan 3 Goku drawing #anime #dbz16 julho 2024 -
 3D printable Akuma no mi: Hana Hana no Mi PROP (Nico Robin Flower16 julho 2024
3D printable Akuma no mi: Hana Hana no Mi PROP (Nico Robin Flower16 julho 2024 -
 Nissan GTR iPhone Wallpaper Nissan gtr, Nissan, Nissan gt16 julho 2024
Nissan GTR iPhone Wallpaper Nissan gtr, Nissan, Nissan gt16 julho 2024 -
 Indian film accused of copying One Piece Film: RED poster design16 julho 2024
Indian film accused of copying One Piece Film: RED poster design16 julho 2024 -
 Desenhos de Melhores Amigos para Sempre para Colorir16 julho 2024
Desenhos de Melhores Amigos para Sempre para Colorir16 julho 2024 -
 Super Saiyan Blue Vegeta Universal Survival png16 julho 2024
Super Saiyan Blue Vegeta Universal Survival png16 julho 2024
