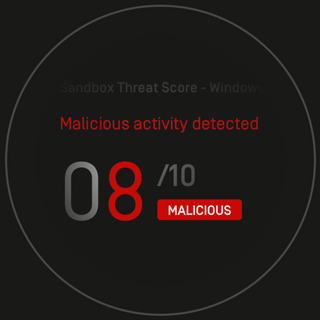
Malware analysis Malicious activity
Por um escritor misterioso
Last updated 18 junho 2024
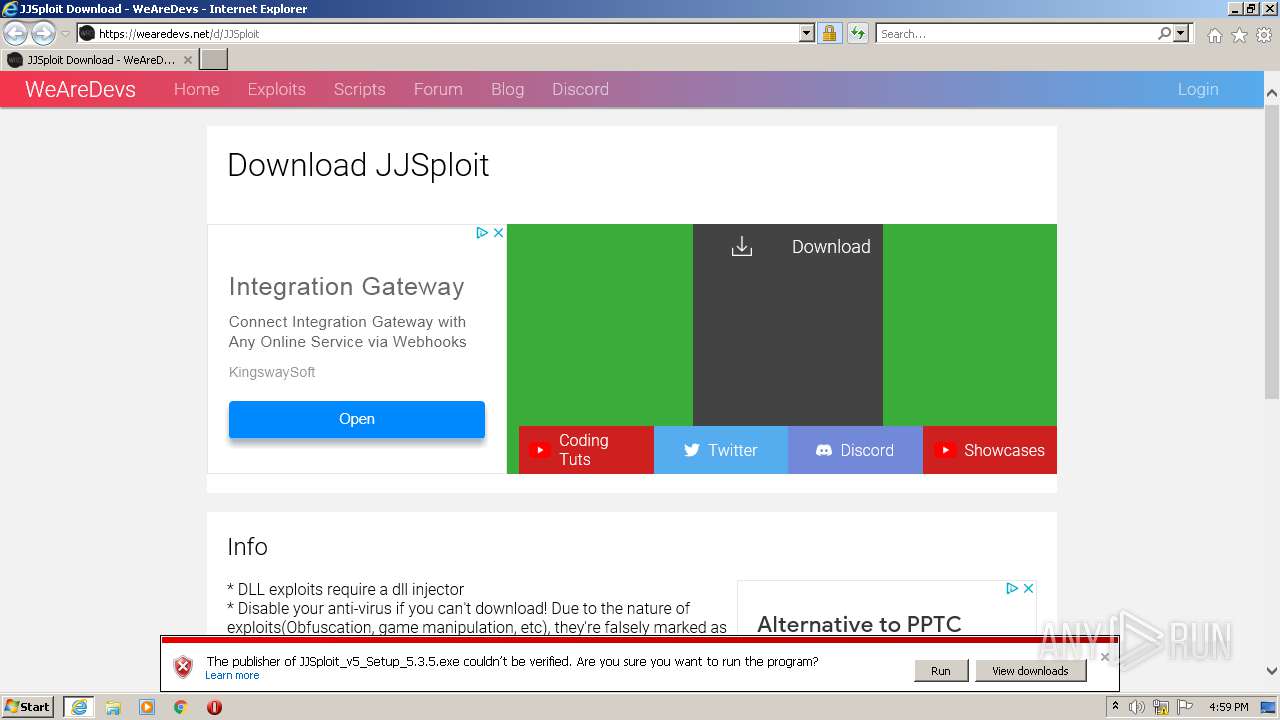

Malware analysis file Malicious activity

Malware analysis mykey_.rar Malicious activity
MetaDefender Cloud Advanced threat prevention and detection
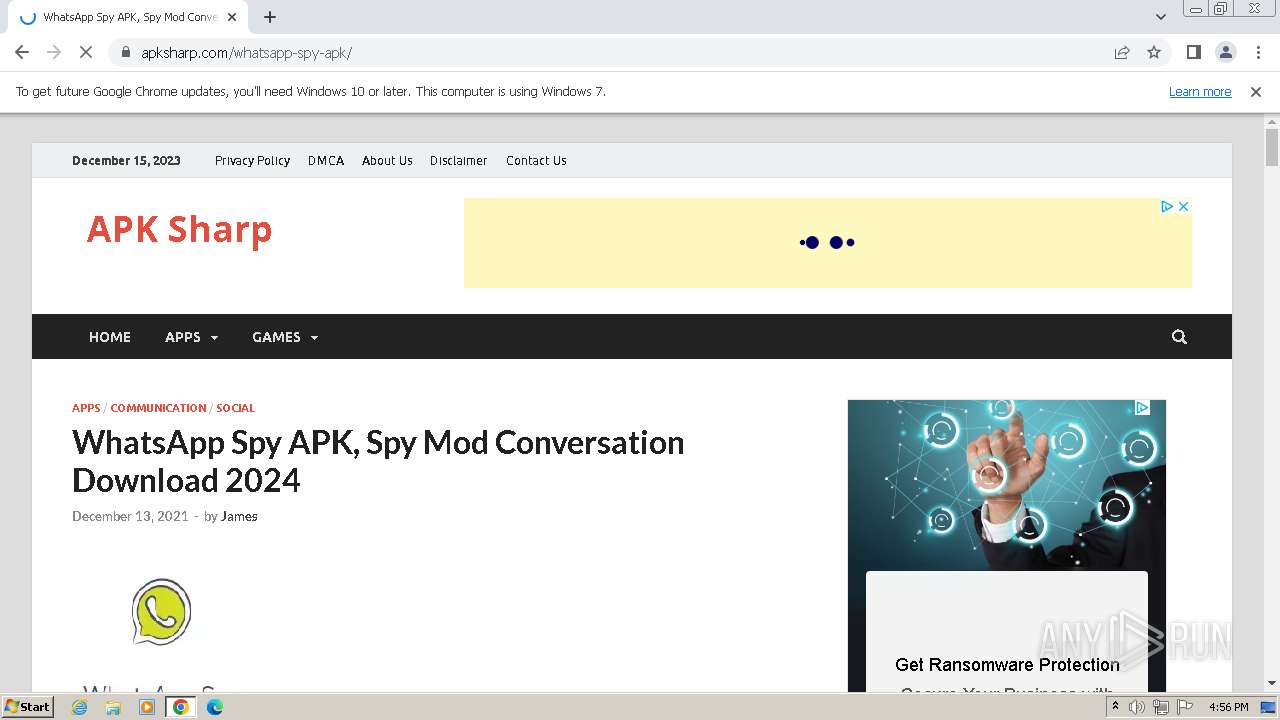
Malware analysis apksharp.com Malicious activity
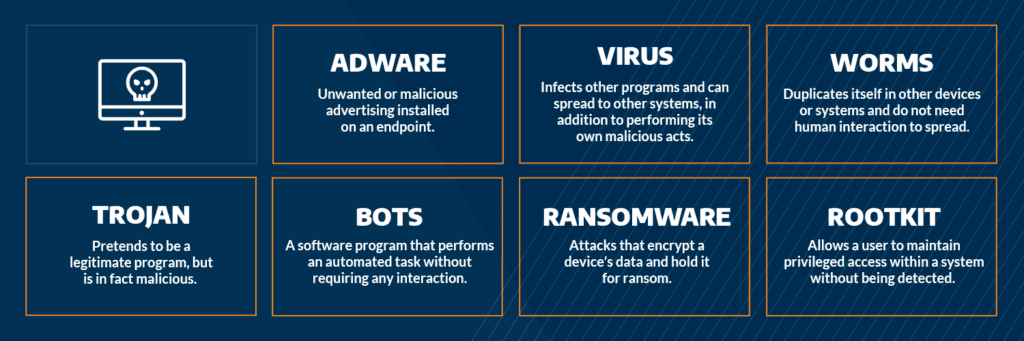
Most Common Malware Attacks
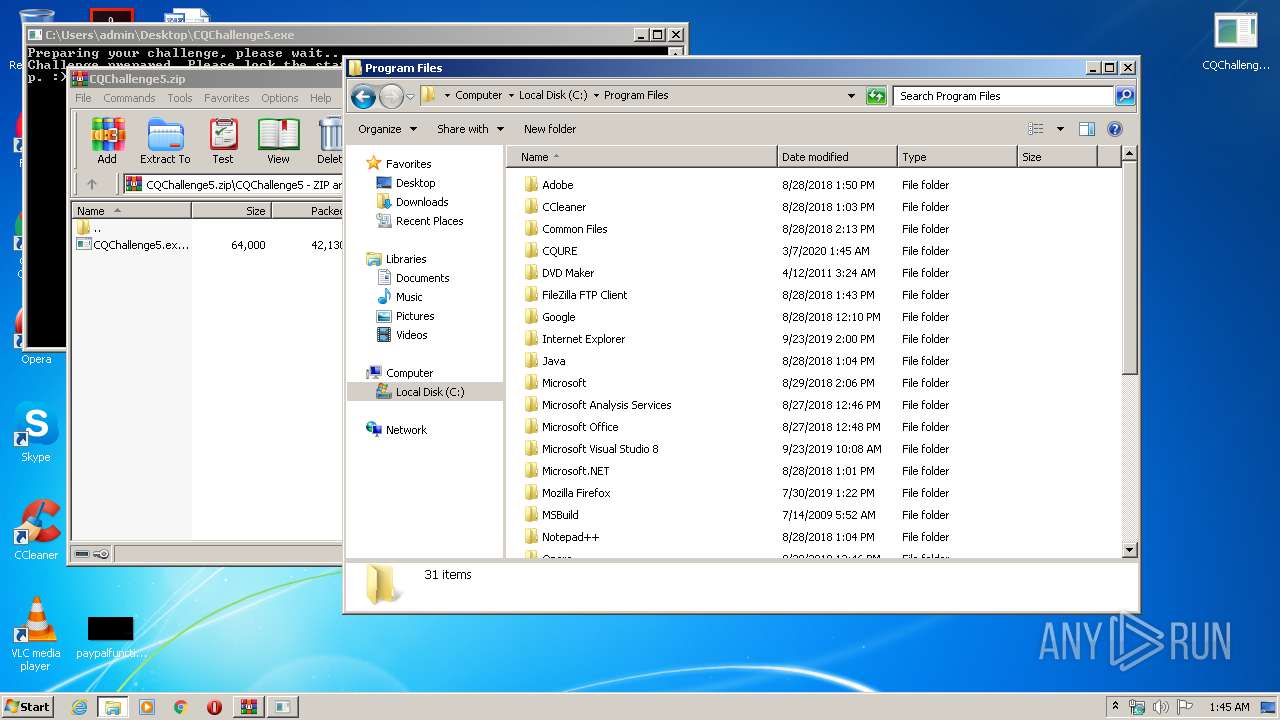
Malware analysis CQChallenge5.zip Malicious activity

Endpoint Detection and Response, Free - What is EDR Security?

Malware Analysis: Steps & Examples - CrowdStrike

Routers Roasting on an Open Firewall: the KV-botnet Investigation

A detailed analysis of the Menorah malware used by APT34
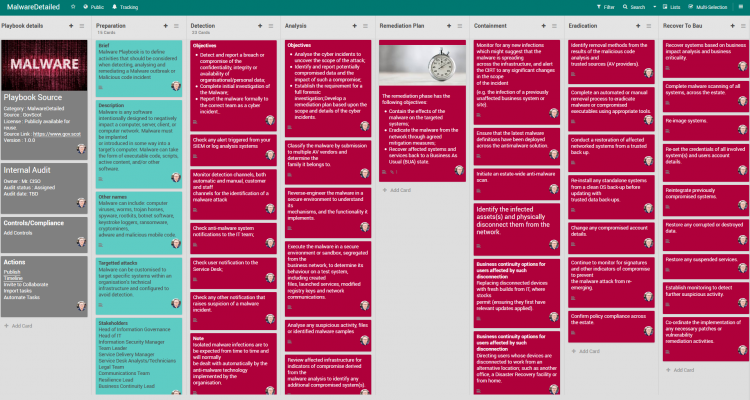
Playbook for Malware outbreak
Recomendado para você
-
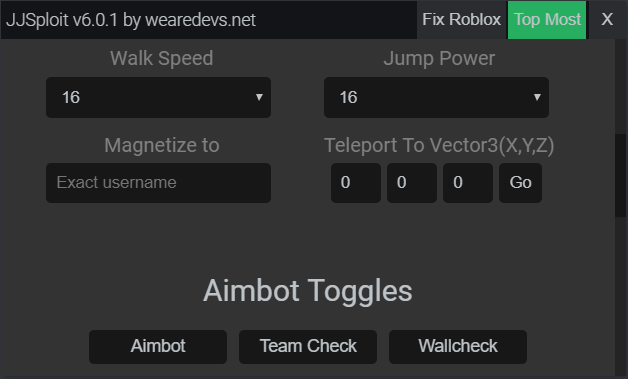 JJSploit Information - WeAreDevs18 junho 2024
JJSploit Information - WeAreDevs18 junho 2024 -
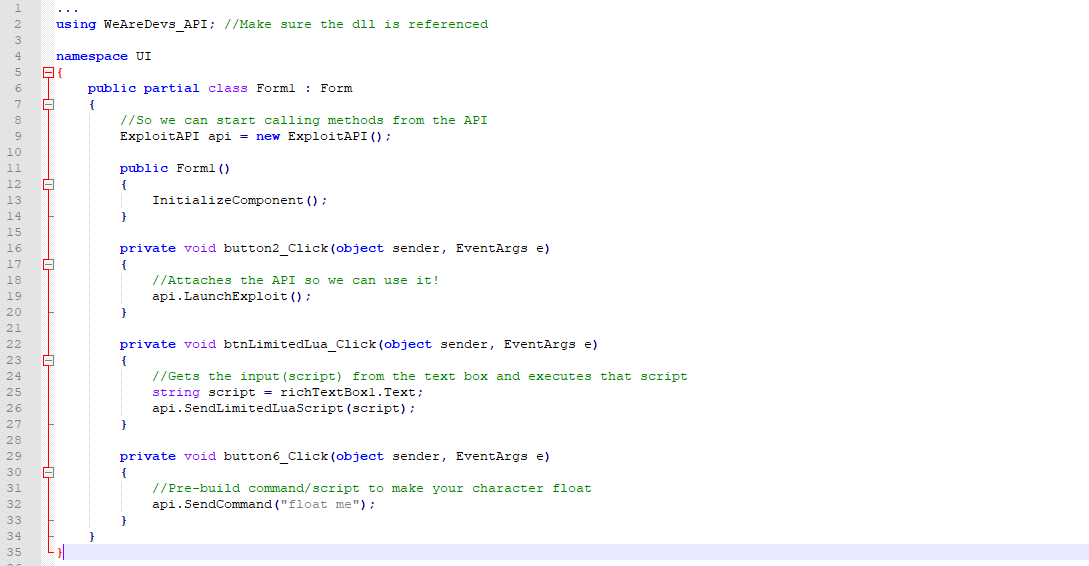 Exploit API C# Documentation & Download - WeAreDevs18 junho 2024
Exploit API C# Documentation & Download - WeAreDevs18 junho 2024 -
wearedevs.net Competitors - Top Sites Like wearedevs.net18 junho 2024
-
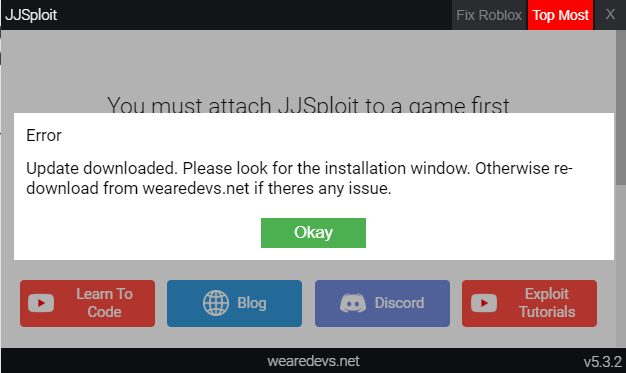 JJSploit Information WeAreDevs, 49% OFF18 junho 2024
JJSploit Information WeAreDevs, 49% OFF18 junho 2024 -
WeAreDevs++ Beta18 junho 2024
-
roblox-executor · GitHub Topics · GitHub18 junho 2024
-
 JJsPLOIT Tutorial #Exploit #tutorial #WeAreDevs #scripting18 junho 2024
JJsPLOIT Tutorial #Exploit #tutorial #WeAreDevs #scripting18 junho 2024 -
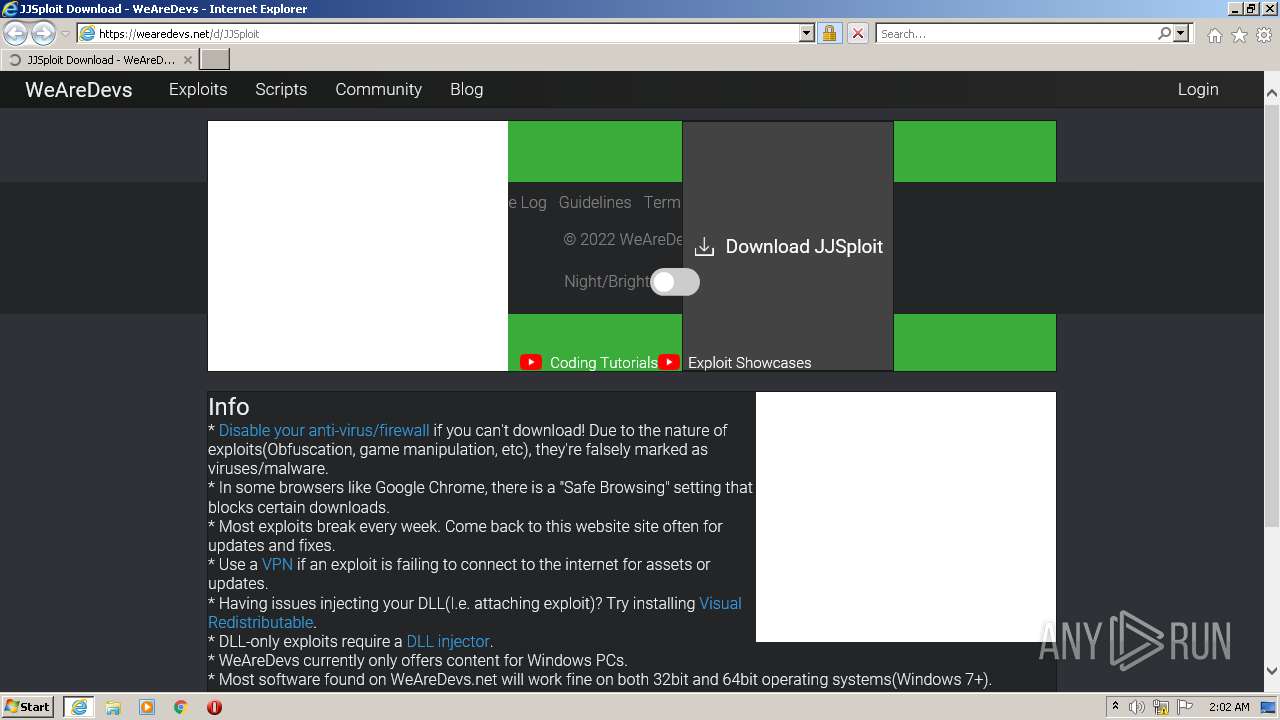 Malware analysis Malicious activity18 junho 2024
Malware analysis Malicious activity18 junho 2024 -
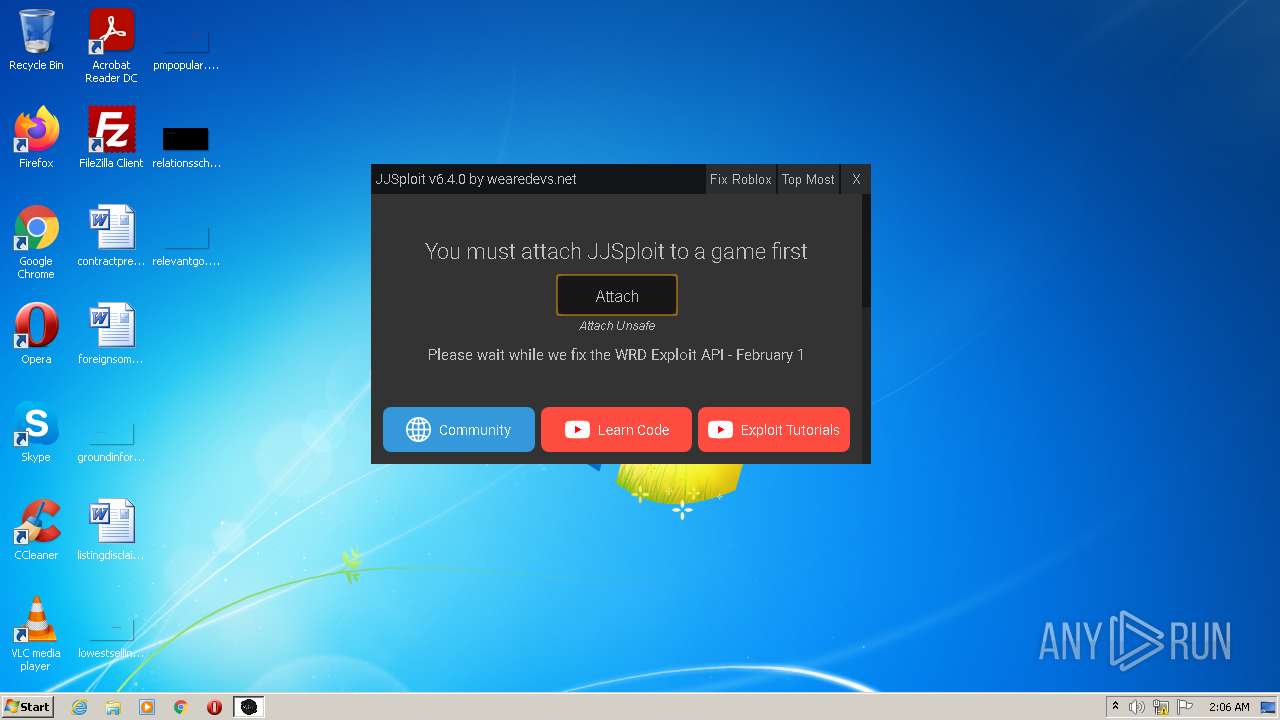 Malware analysis Malicious18 junho 2024
Malware analysis Malicious18 junho 2024 -
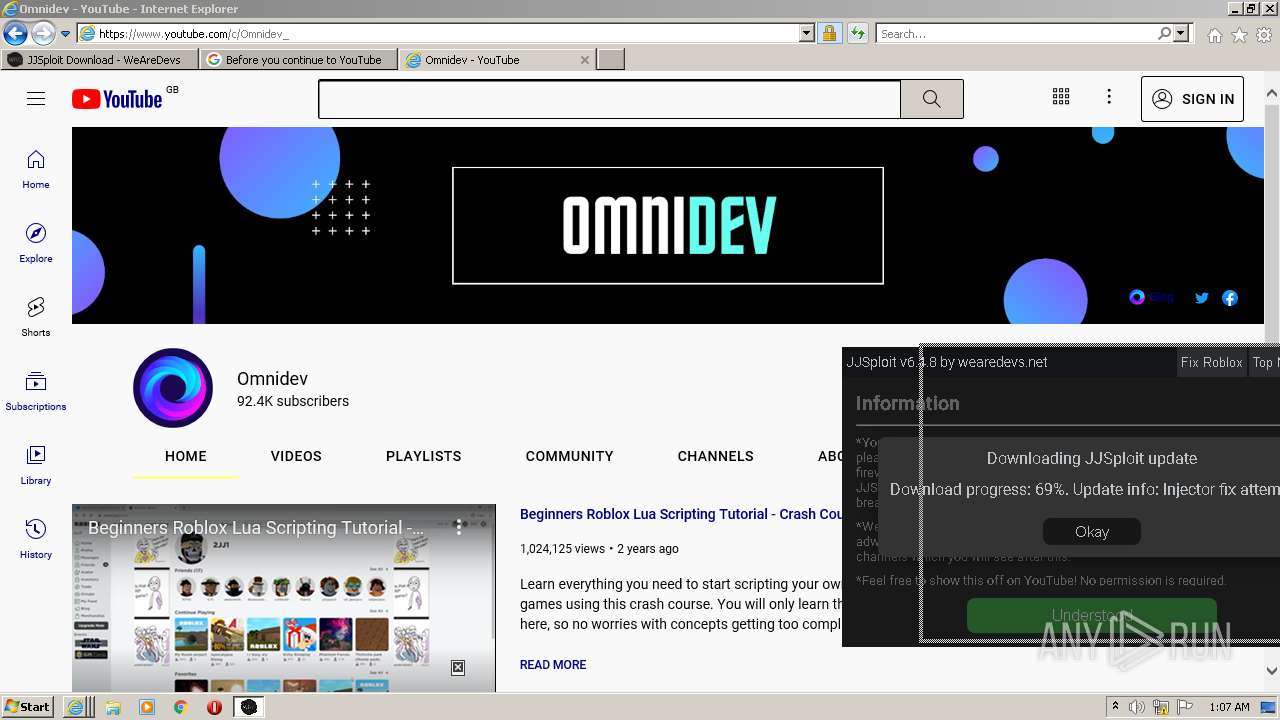 Malware analysis Malicious activity18 junho 2024
Malware analysis Malicious activity18 junho 2024
você pode gostar
-
 Pin by shan ali on Gta v cheats18 junho 2024
Pin by shan ali on Gta v cheats18 junho 2024 -
 WANDINHA ADDAMS DO FILME OU DA SERIE NETFLIX? I Jogo18 junho 2024
WANDINHA ADDAMS DO FILME OU DA SERIE NETFLIX? I Jogo18 junho 2024 -
 Festa di San Giovanni XXIII 2019 - Seminario Vescovile di Bergamo18 junho 2024
Festa di San Giovanni XXIII 2019 - Seminario Vescovile di Bergamo18 junho 2024 -
 Backrooms Descent: Horror Game on Steam18 junho 2024
Backrooms Descent: Horror Game on Steam18 junho 2024 -
 Homem-Aranha agachado e atento - Spiderman - Just Color Crianças : Páginas para colorir para crianças18 junho 2024
Homem-Aranha agachado e atento - Spiderman - Just Color Crianças : Páginas para colorir para crianças18 junho 2024 -
 Build Conway's Game of Life With Python – Real Python18 junho 2024
Build Conway's Game of Life With Python – Real Python18 junho 2024 -
 Ink!Sans, UnderVerse Wiki18 junho 2024
Ink!Sans, UnderVerse Wiki18 junho 2024 -
 CDJapan : A Chivalry of the Failed Knight (Rakudai Kishi no18 junho 2024
CDJapan : A Chivalry of the Failed Knight (Rakudai Kishi no18 junho 2024 -
 Laura's Miscellaneous Musings: Tonight's Movie: The Breaking Point (1950) at the Noir City Film Festival18 junho 2024
Laura's Miscellaneous Musings: Tonight's Movie: The Breaking Point (1950) at the Noir City Film Festival18 junho 2024 -
 Subway Surfers Zurich 2021 Gameplay - Easter Special (Kiloo Games / Play on Poki)🐇18 junho 2024
Subway Surfers Zurich 2021 Gameplay - Easter Special (Kiloo Games / Play on Poki)🐇18 junho 2024