Initial access broker repurposing techniques in targeted attacks
Por um escritor misterioso
Last updated 16 julho 2024

Describing activities of a crime group attacking Ukraine.

What is Authentication Attack? - GeeksforGeeks

A WINDOW INTO RUSSIAN SPEAKING CYBERCRIME by Tim Bobak
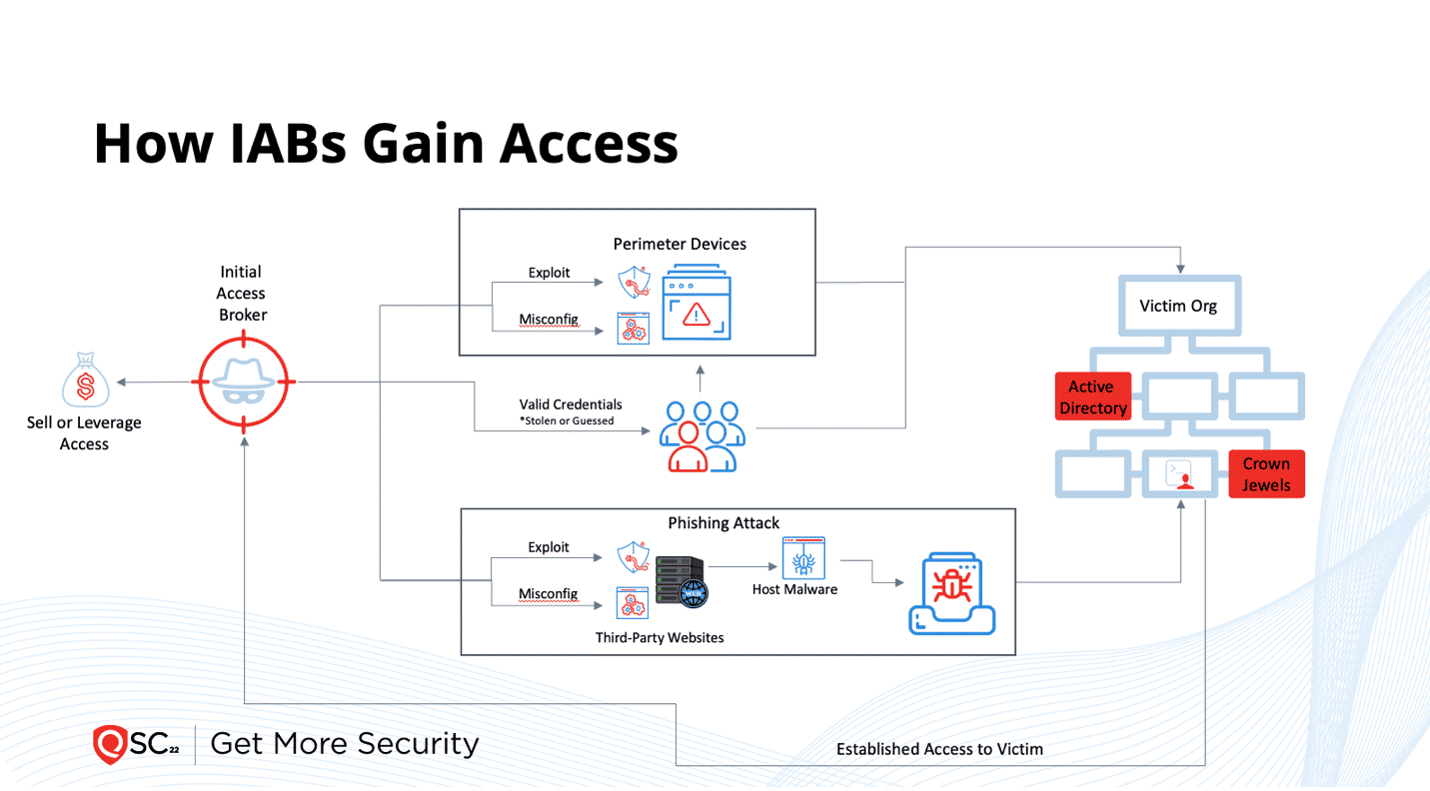
Cybersecurity Risk Fact #3: Initial Access Brokers Attack What Organizations Ignore

⚖️ LWIL #25: Copyright Claims Board, Algorithm Lawsuits, Location Data Rules and More
Cybersecurity Risk Fact #3: Initial Access Brokers Attack What Organizations Ignore

Cisco Umbrella discovers evolving cyberthreats in first half of 2020

A survey on recent optimal techniques for securing unmanned aerial vehicles applications - Syed - 2021 - Transactions on Emerging Telecommunications Technologies - Wiley Online Library
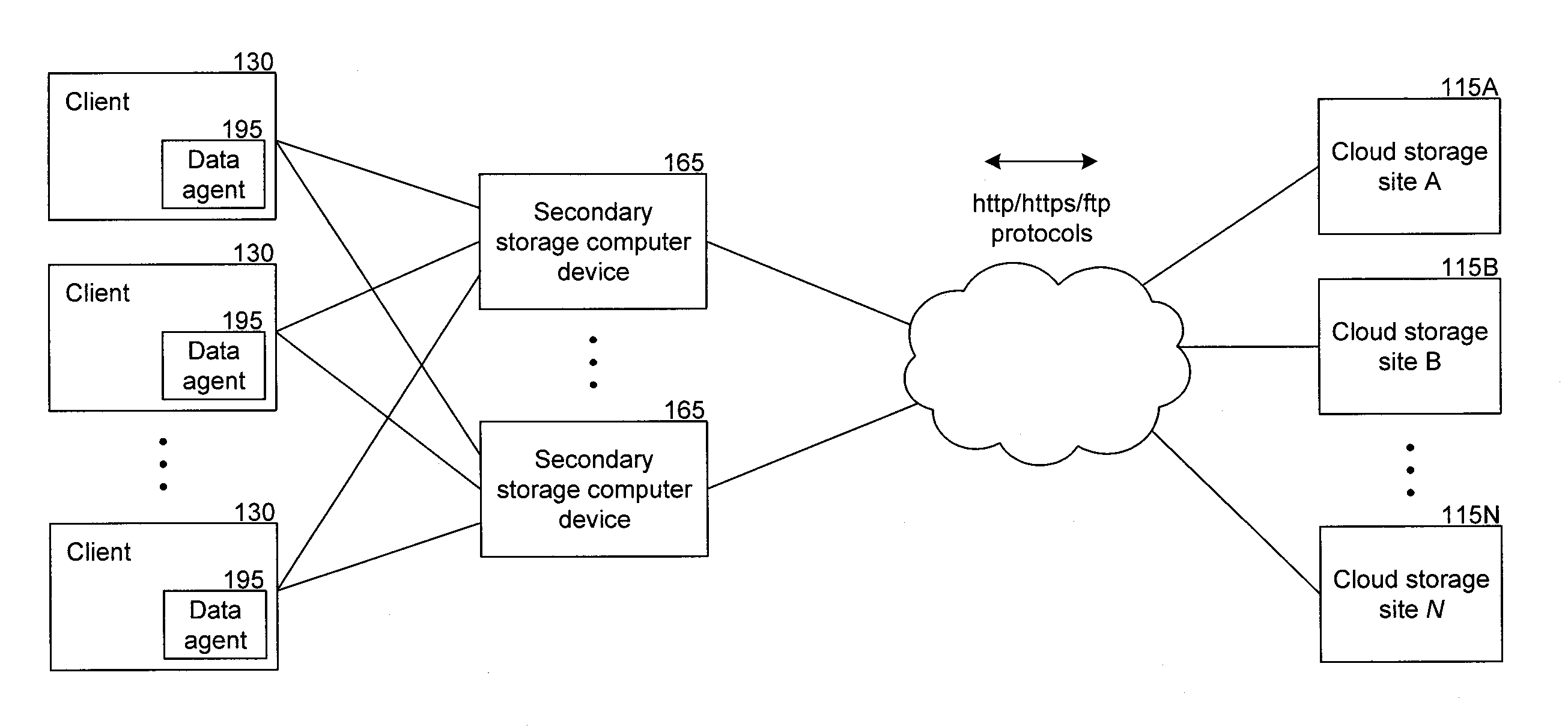
US20100332456A1 - Data object store and server for a cloud storage environment, including data deduplication and data management across multiple cloud storage sites - Google Patents

The State of Healthcare Cybersecurity: VMware Carbon Black Explores the Surge in Cyber Threats

Initial access broker repurposing techniques in targeted attacks against Ukraine
New Report: Risky Analysis: Assessing and Improving AI Governance Tools
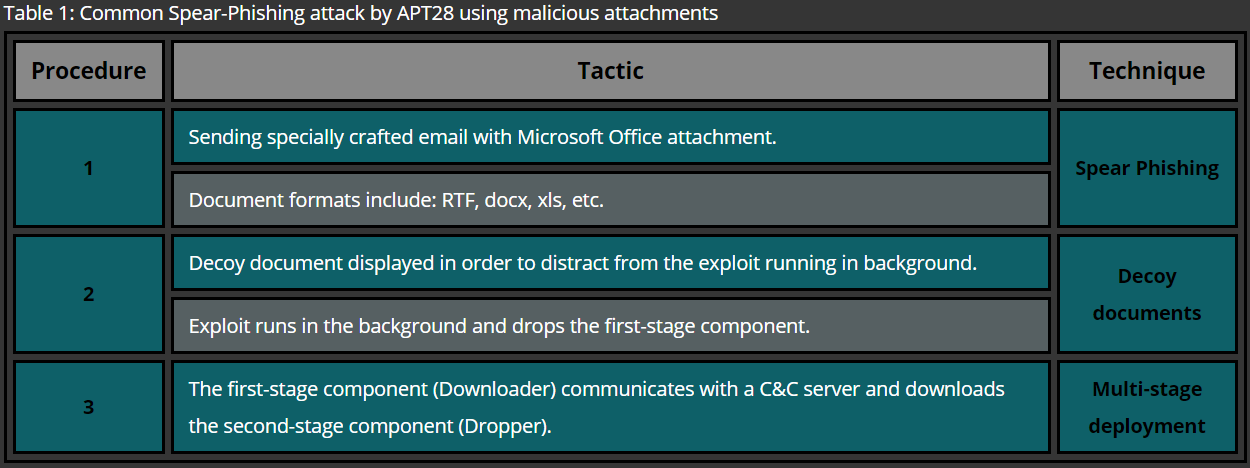
Initial Compromise
GitHub - CyberMonitor/APT_CyberCriminal_Campagin_Collections: APT & CyberCriminal Campaign Collection
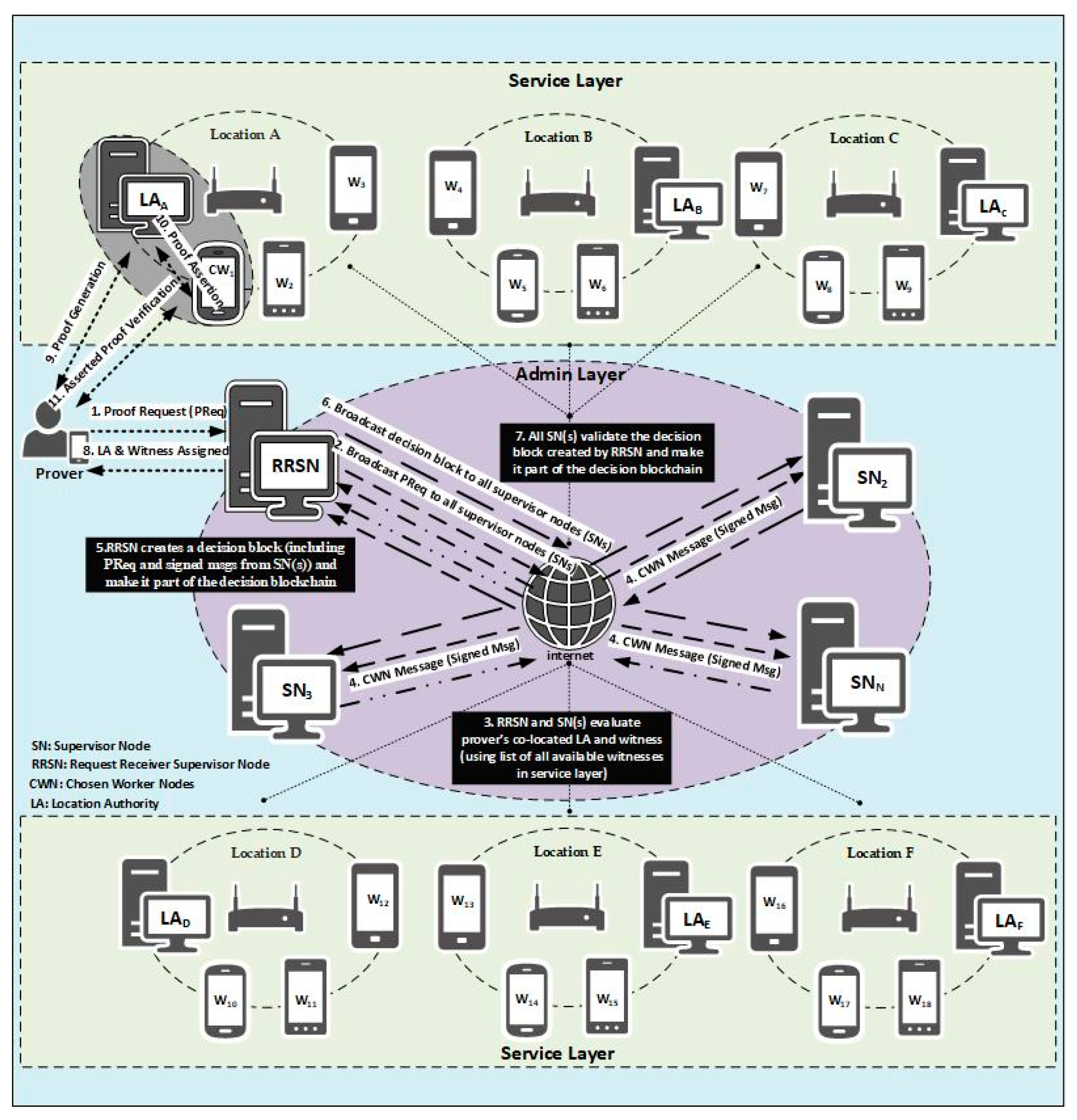
Sensors, Free Full-Text

So long and thanks for all the 0day, NCC Group Research Blog
Recomendado para você
-
![The 7 Most Useful Data Analysis Techniques [2024 Guide]](https://d3mm2s9r15iqcv.cloudfront.net/en/wp-content/uploads/2021/01/data-analysis-qualitative-quantitative.jpg) The 7 Most Useful Data Analysis Techniques [2024 Guide]16 julho 2024
The 7 Most Useful Data Analysis Techniques [2024 Guide]16 julho 2024 -
Analysis Group16 julho 2024
-
Analysis Group16 julho 2024
-
 Analysis Group Office Photos16 julho 2024
Analysis Group Office Photos16 julho 2024 -
 Working at Analysis Group16 julho 2024
Working at Analysis Group16 julho 2024 -
IAG, Image Analysis Group16 julho 2024
-
 Analysis Group London16 julho 2024
Analysis Group London16 julho 2024 -
 Annual Meeting of the Lunar Exploration Analysis Group16 julho 2024
Annual Meeting of the Lunar Exploration Analysis Group16 julho 2024 -
 Analysis Group16 julho 2024
Analysis Group16 julho 2024 -
 Summer Associate Intern - Analysis Group16 julho 2024
Summer Associate Intern - Analysis Group16 julho 2024
você pode gostar
-
 One Piece ganha calendários oficiais de 202116 julho 2024
One Piece ganha calendários oficiais de 202116 julho 2024 -
 Funko Plush: Five Nights at Freddy's Spring Colorway - Cupcake16 julho 2024
Funko Plush: Five Nights at Freddy's Spring Colorway - Cupcake16 julho 2024 -
 Redondo Ave Script Font - Hoodzpah16 julho 2024
Redondo Ave Script Font - Hoodzpah16 julho 2024 -
 Home - Summer Page - Acquaplus Waterpark - Hersonissos Crete16 julho 2024
Home - Summer Page - Acquaplus Waterpark - Hersonissos Crete16 julho 2024 -
Anime Brasil16 julho 2024
-
 Garoar Significado - Dictio - Dicionário Online16 julho 2024
Garoar Significado - Dictio - Dicionário Online16 julho 2024 -
 The 4 Best Places to Buy MTG Arena Codes Online - Draftsim16 julho 2024
The 4 Best Places to Buy MTG Arena Codes Online - Draftsim16 julho 2024 -
 Navegador, Board Game16 julho 2024
Navegador, Board Game16 julho 2024 -
 O poema lido pode ser dividido em duas partes distintas. Identifique-as16 julho 2024
O poema lido pode ser dividido em duas partes distintas. Identifique-as16 julho 2024 -
 Ditto16 julho 2024
Ditto16 julho 2024



