How Do MAC Spoofing Attacks Work?
Por um escritor misterioso
Last updated 16 julho 2024

In this blog, we will go into the complexities of MAC spoofing, analyzing its repercussions and emphasizing the importance of having strong security policies in place.

IP address spoofing - Wikipedia

Lesson 9 - Securing the Local Area Network

ARP Spoofing - What is it and how can I protect myself?

MAC Address Spoofing for Bluetooth - The Security Buddy

What is a MAC address, and what can it reveal about you?
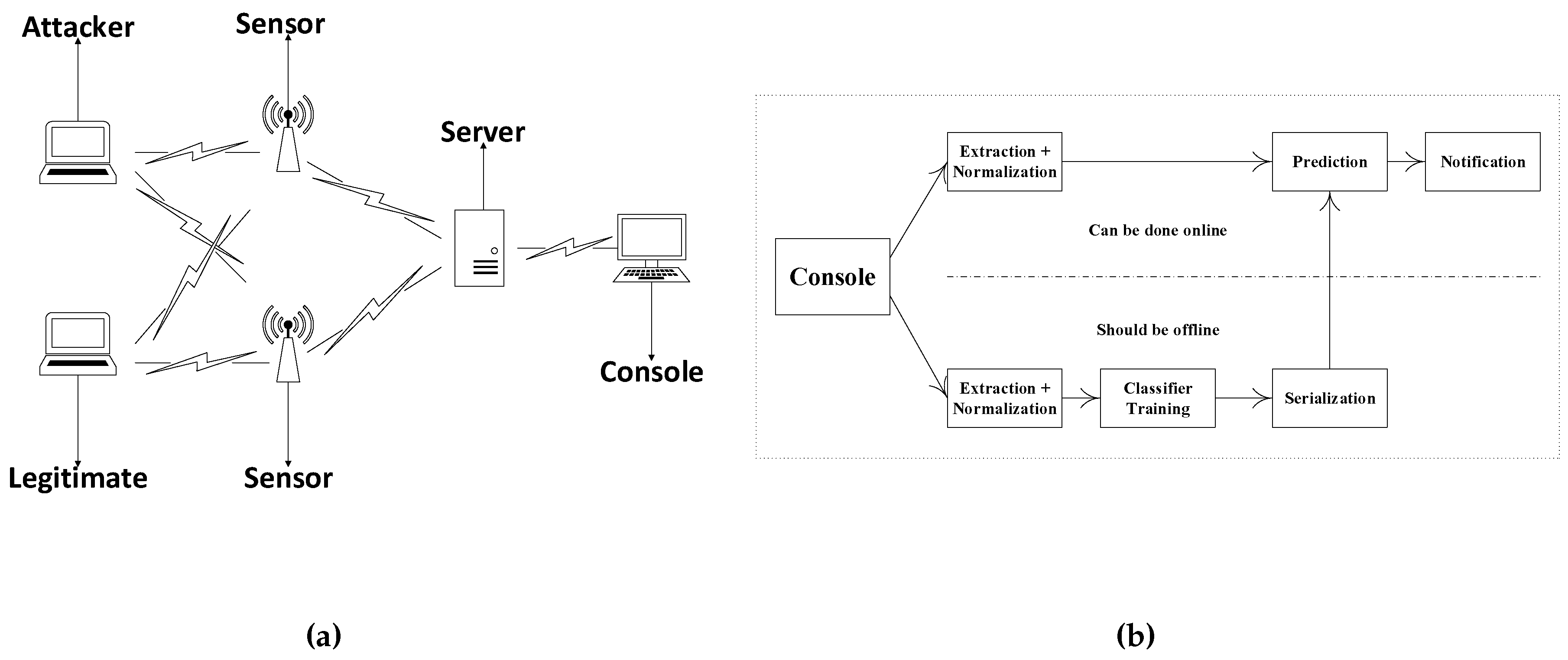
Sensors, Free Full-Text
MAC Spoofing: Understanding and Preventing Unauthorized Network Access - FasterCapital
What is a MAC Address and How Do I Find It?

What is a MAC address, and what can it reveal about you?

What is Spoofing Attack and How to Prevent It? - SOCRadar® Cyber Intelligence Inc.

How To Prevent Spoofing Attacks and Understand the Main Types
Recomendado para você
-
 Redengine Lifetime - Melhor Modmenu Para Fivem - Gta - DFG16 julho 2024
Redengine Lifetime - Melhor Modmenu Para Fivem - Gta - DFG16 julho 2024 -
 What is Spoofing? - FFCCU Blog16 julho 2024
What is Spoofing? - FFCCU Blog16 julho 2024 -
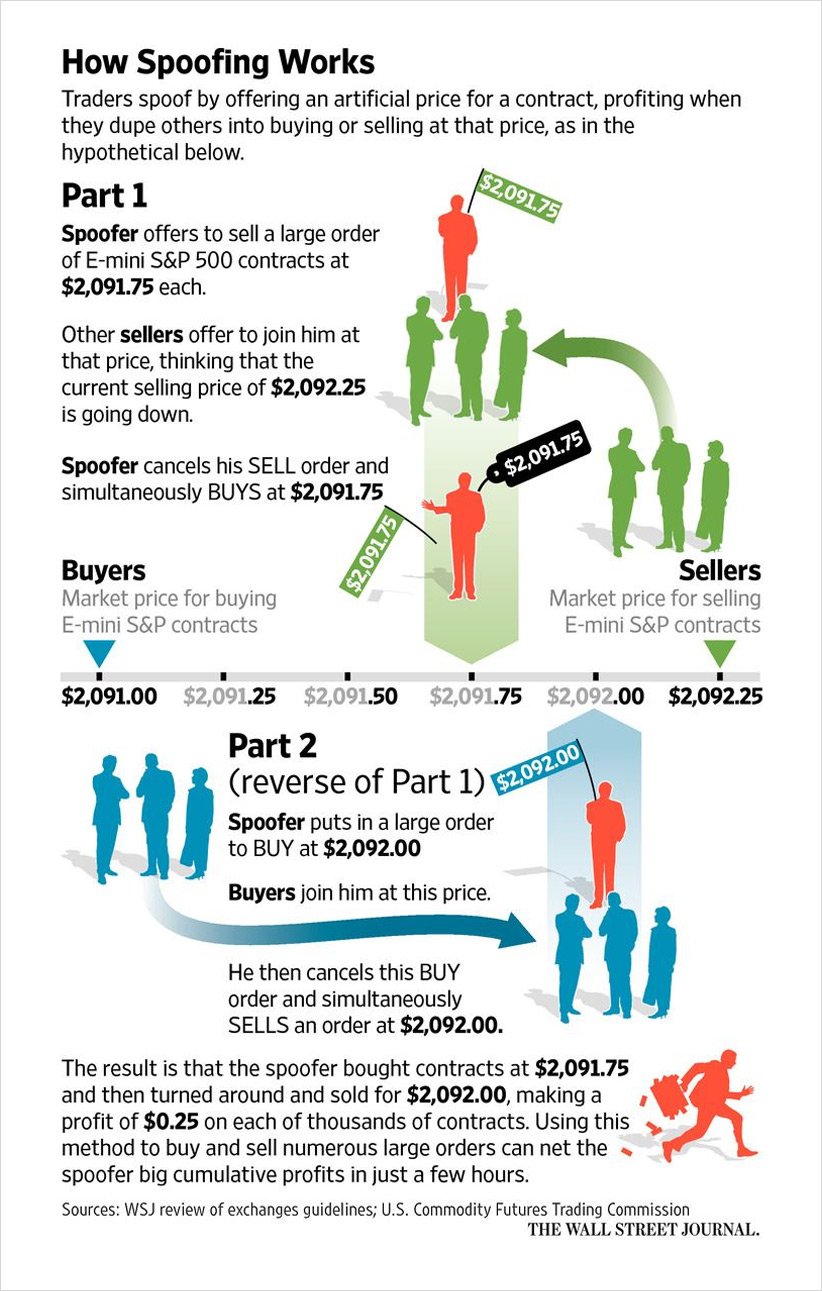 Explaining and Exploring Spoofing - Deribit Insights16 julho 2024
Explaining and Exploring Spoofing - Deribit Insights16 julho 2024 -
 CAIDA Catalog Search - A Collection of Scientific Research on the16 julho 2024
CAIDA Catalog Search - A Collection of Scientific Research on the16 julho 2024 -
 SimGEN Simulator and PNT Product Improvements - Spirent16 julho 2024
SimGEN Simulator and PNT Product Improvements - Spirent16 julho 2024 -
 James the Red Engine, Movie Spoof Films Wikia16 julho 2024
James the Red Engine, Movie Spoof Films Wikia16 julho 2024 -
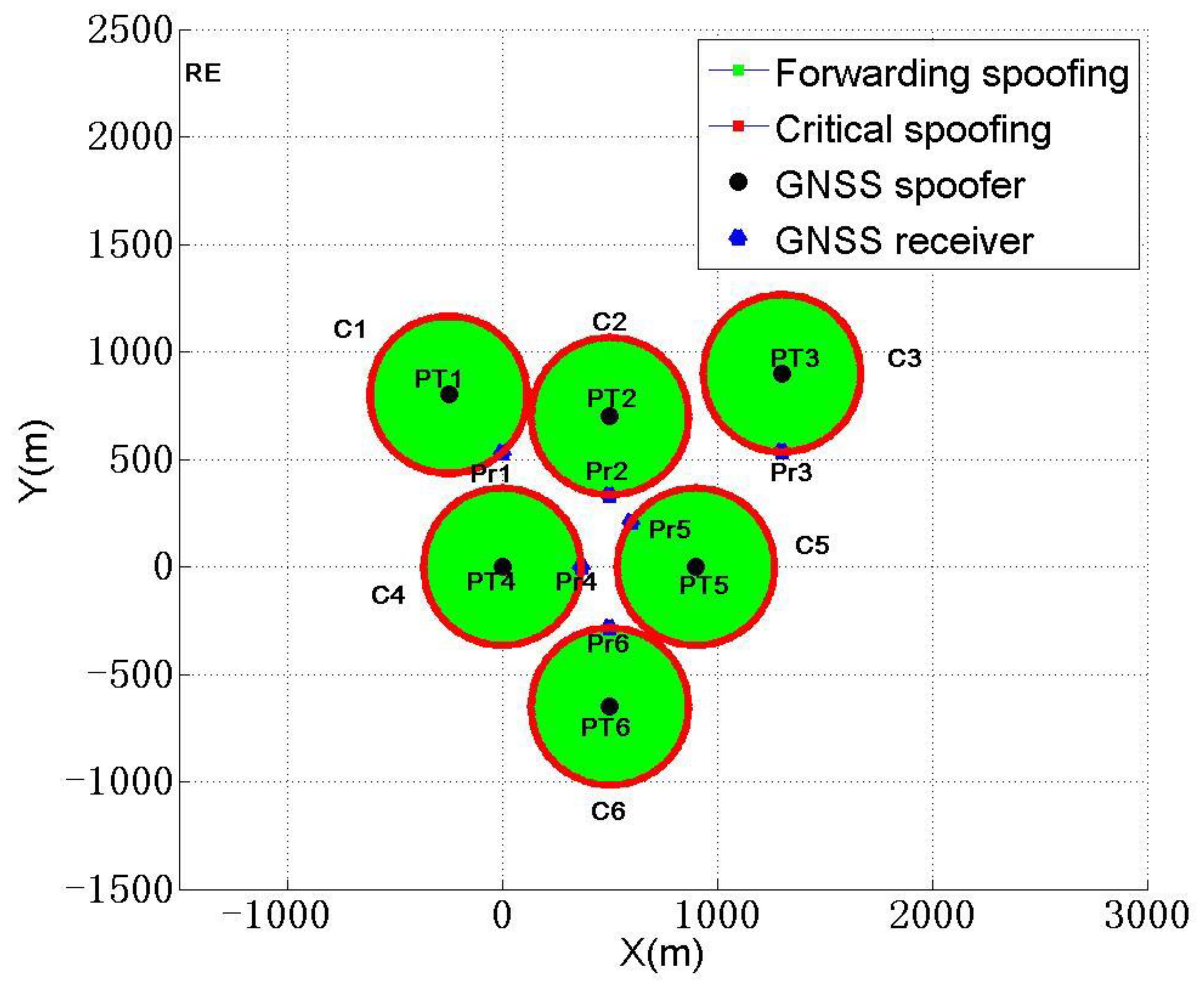 Sensors, Free Full-Text16 julho 2024
Sensors, Free Full-Text16 julho 2024 -
 Licensing16 julho 2024
Licensing16 julho 2024 -
 US7814533B2 - Secure customer interface for Web based data management - Google Patents16 julho 2024
US7814533B2 - Secure customer interface for Web based data management - Google Patents16 julho 2024 -
![Release] Warzone Spoofer](https://imgur.com/ByHppzY.jpg) Release] Warzone Spoofer16 julho 2024
Release] Warzone Spoofer16 julho 2024
você pode gostar
-
 Crítica Stranger Things Final consagra 4ª temporada como mais16 julho 2024
Crítica Stranger Things Final consagra 4ª temporada como mais16 julho 2024 -
 belle delphine janice|TikTok Search16 julho 2024
belle delphine janice|TikTok Search16 julho 2024 -
 Gogeta Ssj4 GT runs a Dbs Manga gauntlet16 julho 2024
Gogeta Ssj4 GT runs a Dbs Manga gauntlet16 julho 2024 -
 Bakugan Battle Brawlers DVD Anime Series Volume 1 Episodes 1-516 julho 2024
Bakugan Battle Brawlers DVD Anime Series Volume 1 Episodes 1-516 julho 2024 -
 Tensei Shitara Slime – Continuação em filme ganha trailer da16 julho 2024
Tensei Shitara Slime – Continuação em filme ganha trailer da16 julho 2024 -
 Halloween map for RTC Con - Creations Feedback - Developer Forum16 julho 2024
Halloween map for RTC Con - Creations Feedback - Developer Forum16 julho 2024 -
 Cosmetics/Boxy Boo, Poppy Playtime Wiki16 julho 2024
Cosmetics/Boxy Boo, Poppy Playtime Wiki16 julho 2024 -
 FI Unboxing (Lyrics & Credits) - Imgur16 julho 2024
FI Unboxing (Lyrics & Credits) - Imgur16 julho 2024 -
 Lego Star Wars: The Skywalker Saga16 julho 2024
Lego Star Wars: The Skywalker Saga16 julho 2024 -
 That Time I Got Reincarnated as a Slime the Movie: Scarlet Bond - Rotten Tomatoes16 julho 2024
That Time I Got Reincarnated as a Slime the Movie: Scarlet Bond - Rotten Tomatoes16 julho 2024